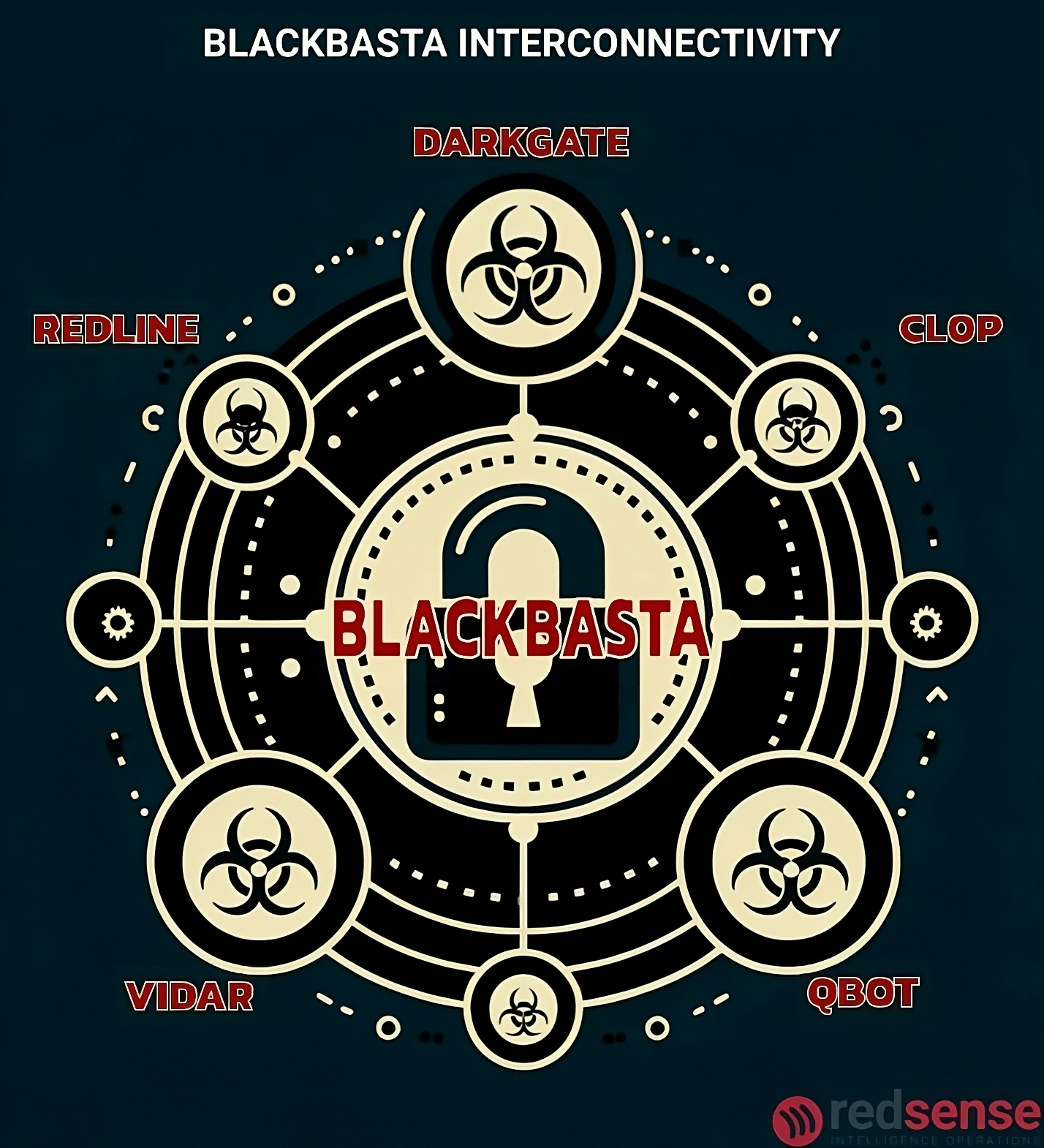
Infographic depicting BlackBasta’s use of multiple separate malware [Source: RedSense]
On October 25, 2024, ReliaQuest reported a new BlackBasta campaign exploiting Microsoft Teams—an addition to an earlier May 2024 campaign impersonating IT staff. This surge in BlackBasta’s social engineering focus isn’t random.
The following blog unpacks the group’s evolving tactics, examining why and how BlackBasta arrived at their current campaigns and where these campaigns will move in the future.
2022: Between Botnets & Social Engineering
As with all post-Conti stories, this one begins with Conti’s dissolution.
When Conti fractured in early 2022, it created a set of offspring who quickly stood out by blending traditional Conti’s tactics with its own emerging identities. BlackBasta’s approach at that point was more traditional. They leaned heavily on Qbot, much as Conti had relied on TrickBot and Ryuk before them. At the same time, BlackBasta’s leadership observed Conti’s shift toward social engineering prior to its breakdown, especially with the rise of callback phishing techniques like BazaarCall.
BazaarCall and Silent Ransom’s Influence
The BazaarCall callback phishing traces back to Silent Ransom, a faction under Conti2 (Royal/BlackSuit), which was pioneered in early 2022. Victims were lured to call a support line number sent via email, where operatives posing as tech support then directed them to install a remote management tool such as Zoho or Atera and give access to their system. By the Winter of 2022, Silent Ransom’s BazaarCall’s success created friction within Conti2, eventually prompting Silent Ransom’s departure. By spring, its influence had spread across the post-Conti landscape, showing that human engineering could be as valuable as botnet delivery in achieving high-yield infiltration.
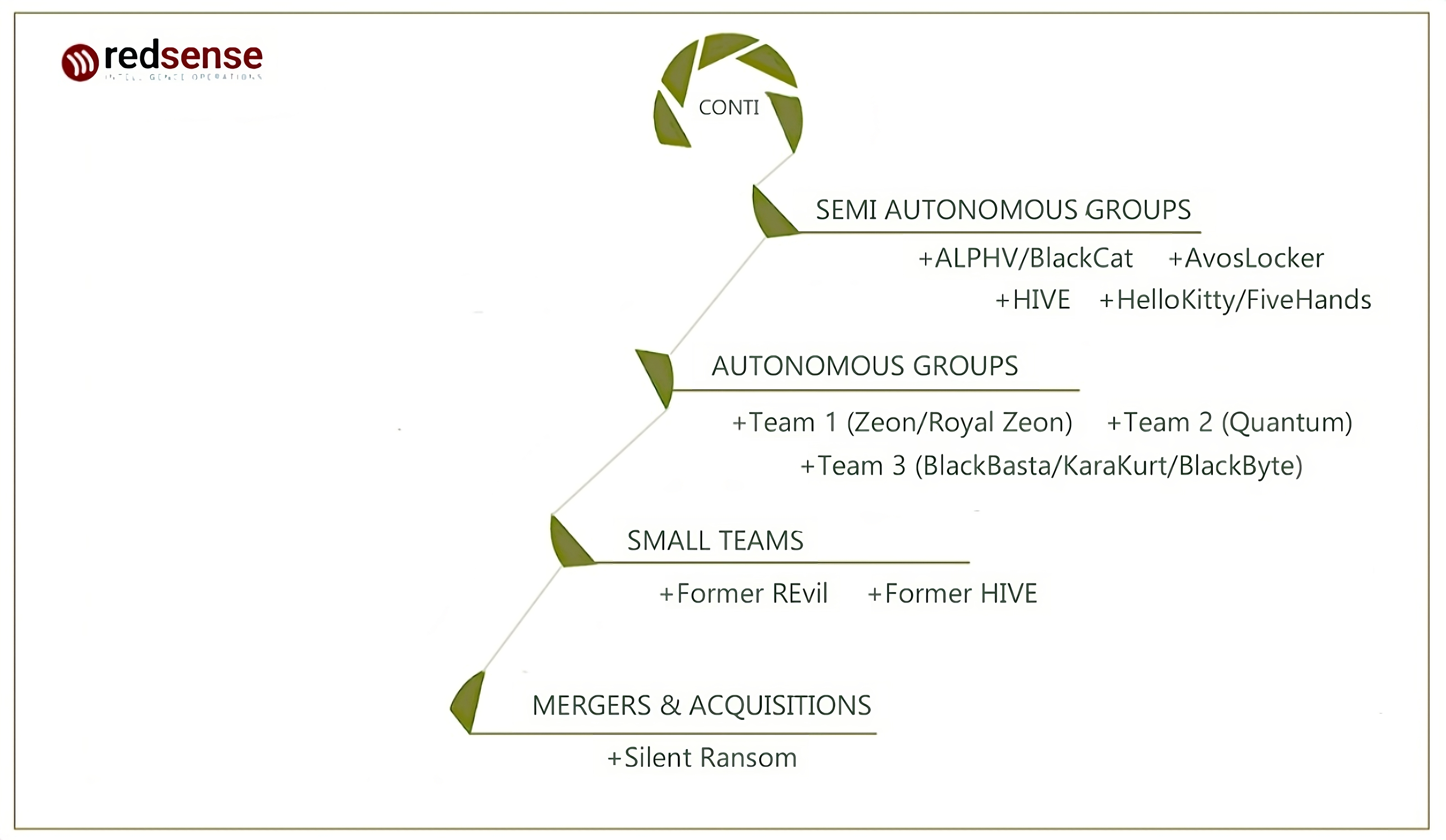
Conti’s disbandment in 2022 resulted in the existence of at least six smaller offshoot groups, including BlackBasta, Quantum (Royal), and Silent Ransom [Source: RedSense]
There are two cases of BazaarCall that are especially relevant to BlackBasta’s current evolution of social engineering schemes.
First is the Royal (formerly Conti2) scheme targeting users of the educational software Udemy:
- Stage One: Victims received a fake “Udemy” email about a subscription renewal, complete with a PDF invoice and support number for cancellation.
- Stage Two: When victims called the number, a Royal operative prompted them to download a “cancellation invoice” file.
- Stage Three: This file contained malware—like Cobalt Strike, AresLoader, or IcedID—that provided Royal with initial access.
- Stage Four: Royal escalated by exfiltrating data and deploying ransomware, leaving victims compromised.
BlackBasta began to utilize this scheme in 2023. As we will see later on, the group then adopted a modified version in 2024, eventually leading to its current MS Teams-targeting model.
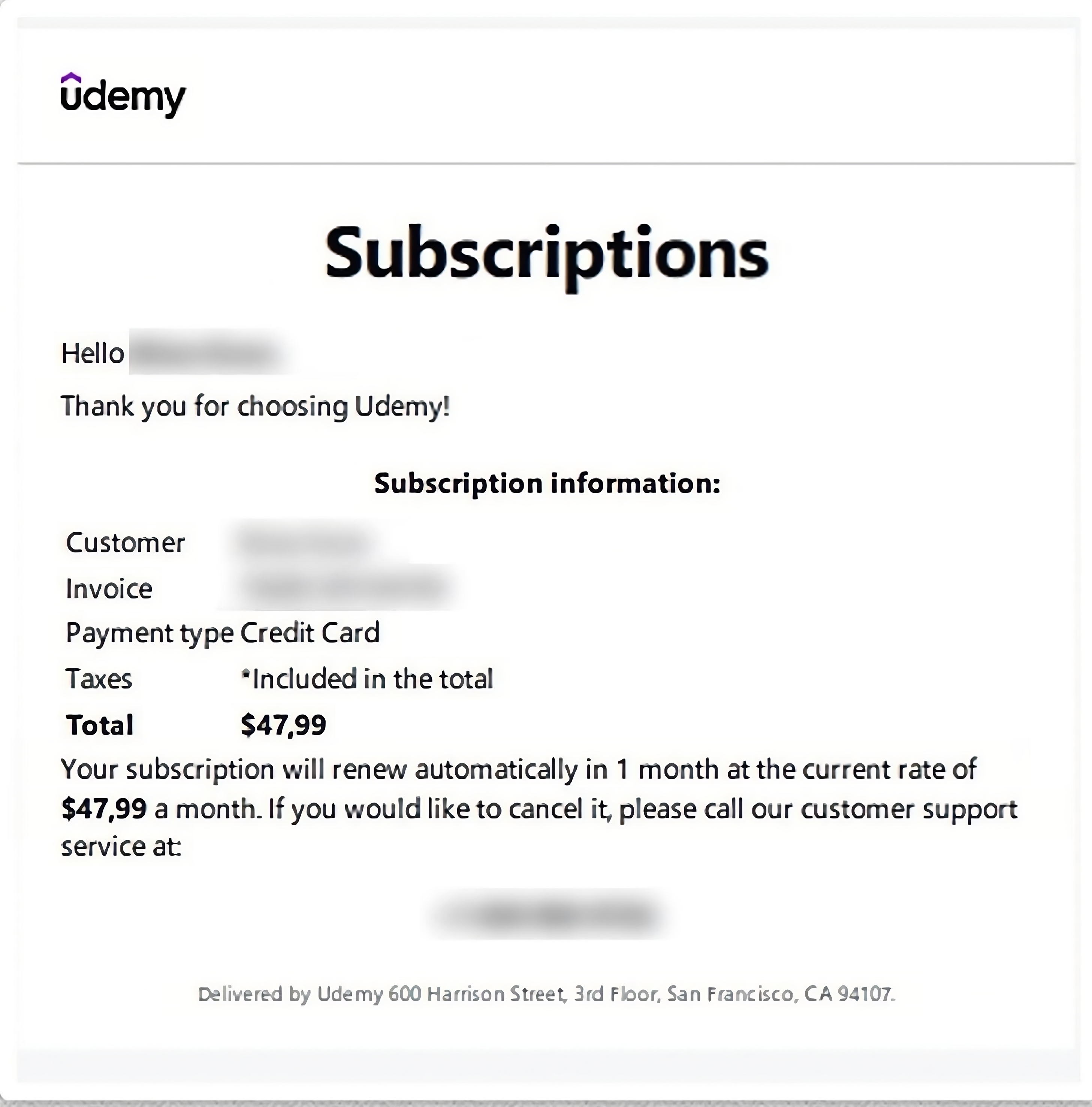
Royal’s fake Udemy invoice [Source: RedSense]
The second case was “email bombing”.
In October 2022, Zeon (Conti1) launched a social engineering attack targeting high-level employees in critical industries with fake security emails. Days after these emails were sent, a Zeon operator posing as IT staff followed up with a call to targets referencing the aforementioned email and raising security concerns. Gaining the employee’s trust as a “security professional,” the operator then persuaded them to start a remote access session using a tool such as Zoho or AnyDesk.
This attack strategy would end up being almost identical to the 2024 BlackBasta tactic reported by ReliaQuest on October 25.
Though BlackBasta engaged with callback phishing back in 2022, its primary focus remained on botnet distribution—a distinction that defined its tactical path. Unlike Silent Ransom or Conti2 (Royal/BlackSuit), BlackBasta relied heavily on Qbot as its primary dissemination tool. Due to Qbot’s resilience, BlackBasta pressed on, largely unaffected. BazaarCall remained a peripheral tactic to the group but not a core strategy.
As such, BlackBasta’s initial experimentation with social engineering in 2022 set the stage for what would become its more complex tactics in 2023 and 2024 (the Udemy-like phishing borrowed from Royal or “email bombing” and IT scam “borrowed” from Zeon). However, in 2022, while Royal and Zeon honed callback phishing, BlackBasta stayed rooted in botnet delivery, favoring scale over precision—a method that would shift in 2023.
2023: Botnets Persist, but with Nuance
In late 2022 and early 2023, Royal and Zeon’s social engineering campaigns reached their respective zeniths. They employed “black SEO” and “Google Dorking” methods to exploit search engine results and amplify their prospective reach—a TTP not even seen in previous Conti campaigns. During this time, Zeon even developed an automated spam engine for Phishing-as-a-Service (PhaaS).
In-depth Investigations on Zeon and Royal social engineering schemes of that time, as well as Zeon PhaaS services, are available to RedSense subscribers.
Compared to this, BlackBasta was not investing in social engineering at all, besides re-shuffling different email templates for the delivery of QBot.
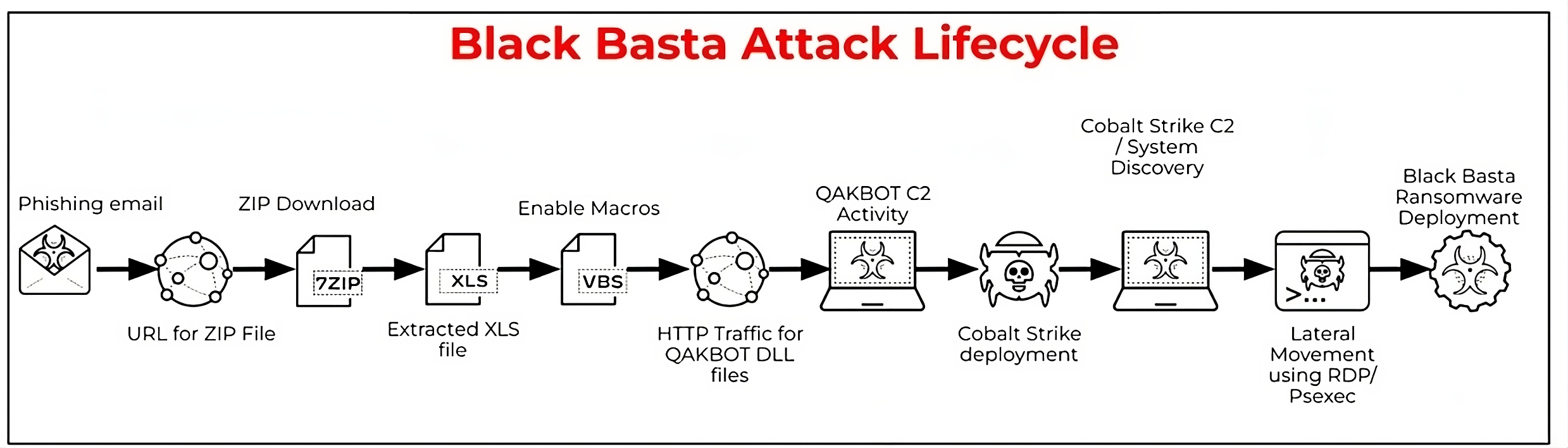
Standard Attack Killchain of BlackBasta in 2023 via HC3’s official threat profile on the group. NOTE: DarkGate replaced Qakbot/Qbot due to Qbot’s takedown.
However, paradoxically, soon after peaking, Conti’s social engineering spree sharply declined. In RedSense’s late February 2023 investigation shared with WSJ, we highlighted that post-Conti groups had cut about 45 call center operators—a surprising move signaling an overall downturn in callback phishing ransomware delivery operations. We concluded that maintaining these call centers had become too costly for the groups to sustain. But this was only the beginning.
By summer, major post-Conti groups had nearly abandoned their social engineering focus:
- Royal, following an attack on the city of Dallas, TX (mimicking its Costa Rica campaign during the Conti rebrand), transformed into BlackSuit and began investing in joint collaborations via a shared malware lab.
- Zeon halted its independent operations, shifting to act as a “ghost group” covertly conducting operations for groups such as Akira and LockBit.
- Lastly, Silent Ransom, the pioneer of the social engineering approach, simply ceased to exist.
Now, BlackBasta’s botnet-focused strategy seemed sound, allowing them to head into their scheduled Summer 2023 vacation without significant concerns. However, in August 2023, a US-led operation seized QBot servers, redirecting botnet traffic to law enforcement-controlled systems and allowing authorities to identify and clean infected machines. Much of this traffic involved BlackBasta’s potential victims, whom they had been infecting in “background mode” over the summer, planning to “harvest” in the fall. Losing these targets was a critical setback that required immediate attention.
BlackBasta had enough flexibility and strength to quickly “jump botnets” from QBot to Darkgate. However, they still had to pick up the pace. This is when we began to see them utilizing new approaches to social engineering and dissemination to compensate for the loss of QBot.
An in-depth investigation of BlackBasta's shift to Darkgate botnets is available to RedSense subscribers.
DarkGate, now aligned with BlackBasta, updated its killchain to broaden its infiltration tactics. In October 2023, right after the creation of the BlackBasta-DarkGate alliance, TrendMicro discovered that DarkGate was moving beyond the use of malicious PDF files for malware deployment—a standard BlackBasta method—and that the loader was now targeting Microsoft Teams and Skype.
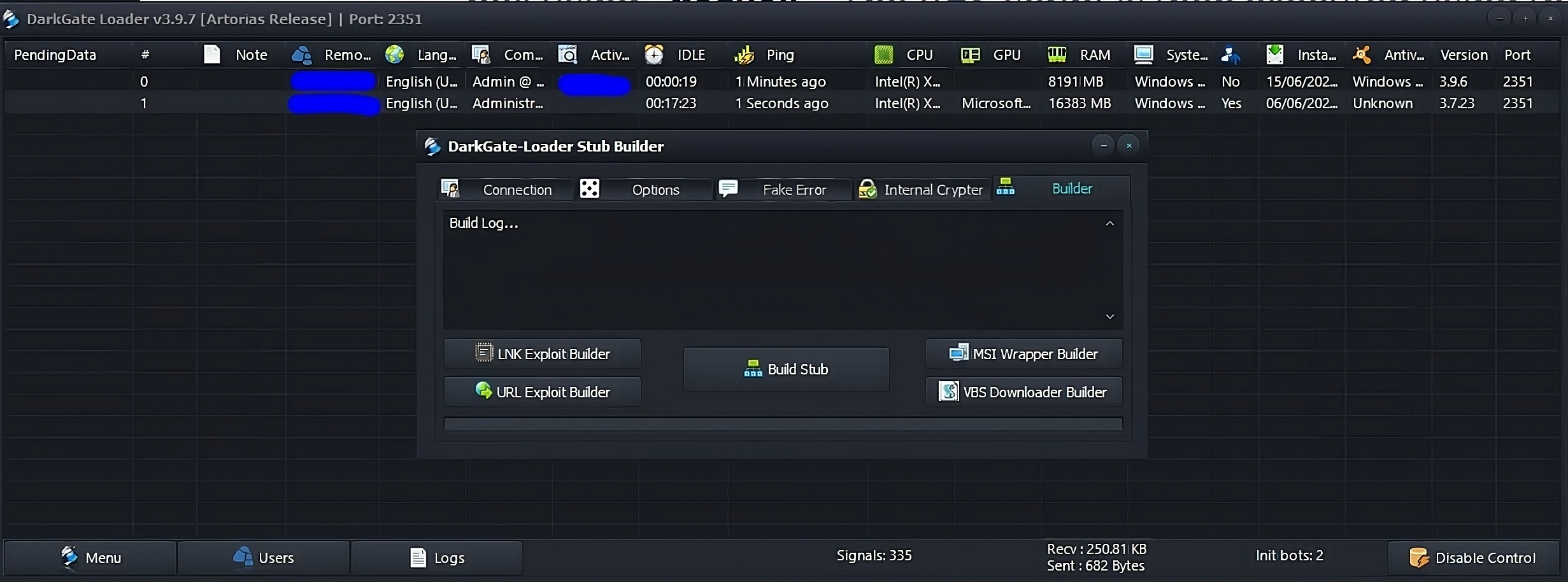
DarkGate’s administrative panel. Among novel features were full support for Cloudflare on port 80, a resilience module, a TaskManager module, and high loader stability.
Note: Targeting Microsoft Teams was precisely the tactic that BlackBasta would prioritize a year later in October 2024. The 2023 TrendMicro research concluded that by shifting to trusted communication platforms, DarkGate exploited routine channels, amplifying its potential to bypass detection and embed within organizational systems. This was the same conclusion noted by ReliaQuest, who discovered BlackBasta’s newest round of MS Teams targeting in 2024.
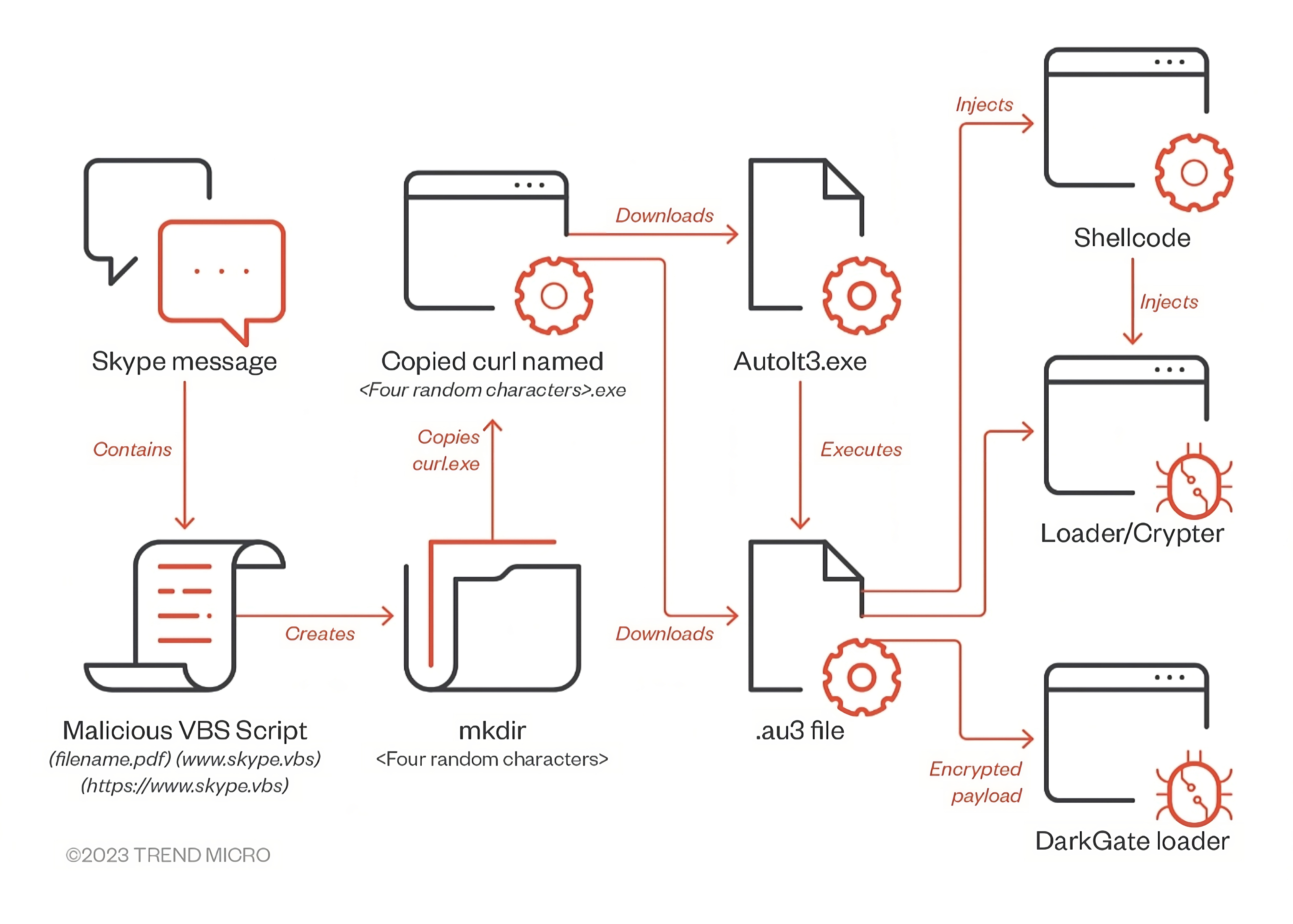
DarkGate infection chain abusing Skype. [Source: TrendMicro]
2024: Targeted Phishing
In early 2024, BlackBasta allegedly engaged in communication with a third-party dissemination specialist working for other post-Conti groups. That month, RedSense uncovered a Cisco, Citrix, and Fortinet impersonation campaign aimed at credential harvesting. Notably, a similar tactic was used a year earlier by Royal and was later adopted by Zeon’s offshoot, INC Ransomware, in this case exclusively impersonating Citrix. While BlackBasta’s scheme may not be an exact copy, its similarity suggests shared methodologies, cross-group influences, and/or shared resources.
A detailed analysis and IOCs related to BlackBasta's Cisco, Citrix and Fortinet impersonation campaign is available to RedSense subscribers.
In May 2024, BlackBasta launched a new impersonation campaign posing as a fictional security vendor to gain remote access to victims’ systems. The campaign involved an operator calling victims and warning them of a fictitious “urgent security incident” that was allegedly affecting their organization. Under this pretense, the operator would instruct victims to install remote access software like Zoho, AnyDesk, or Atera and would then proceed to distract the victim.
After implementing this approach in May, BlackBasta went on its regular summer hiatus in June, pausing further experiments. In September, they resumed the “email bombing” tactic and introduced the Microsoft Teams impersonation, marking the latest developments in their campaigns.
BlackBasta Malware Delivery Evolution
As seen with QBot/DarkGate, BlackBasta’s campaigns heavily rely on the current state of their botnets. Even their recent Citrix and Fortinet impersonations were paired with the introduction of a new “hVNC” and “Citrix-targeting” botnet.
Given their past patterns, it’s likely that after brief experimentation with advanced impersonation, BlackBasta will revert to traditional tactics such as fake vendor login pages for credential theft while still continuing their core investments in botnet delivery and re-weaponizing infostealers as they did earlier in 2023. Although RedLine, one of their regular tools, was recently disrupted by international law enforcement efforts, the group can adapt by shifting entirely to reliance on Vidar and its similar capabilities.
However, external factors could once again continue to steer the group in new directions.
For instance, their October 2024 targeting of Microsoft Teams may not be coincidental and instead be directly connected to the peculiar trend of MS Teams exploits in Russian-speaking cyberspace during 2023–2024.
MS Teams Targeting & Possible Nation-State Influence
April-May 2023: The first notable instance of this trend comes from Nobelium’s May 2023 campaign. In May, Nobelium, also known as Midnight Blizzard—a Russian nation-state APT group—launched a Microsoft Teams campaign that closely resembled BlackBasta’s 2024 tactics: Nobelium contacted victims over Teams, posing as IT support staff to gain their trust. Using tailored messages within Teams, they lured targets into credential theft and system infiltration, taking advantage of the platform’s trusted status.
Interestingly, just a month earlier, in April 2023, BlackBasta targeted UK critical infrastructure, specifically Capita—a key contractor for the UK Ministry of Defence and NHS. They disabled Microsoft 365 services, including Teams, email, and core functions, potentially accessing Teams data and emails for post-breach activities. [Note: It remains unclear if these events were directly connected.]
July 2023: In July, a RAMP ransomware forum post exposed new methods for exploiting MS Teams’s security gaps, allowing attackers to bypass its backend validation on critical functions.
Techniques covered in this post enabled attackers to alter messages or disguise malicious files, tricking victims into unauthorized actions or downloads.
Also in July, Storm-0324, a known Initial Access Broker (IAB), was reported using Teams to distribute phishing links. By leveraging Teams’ integration with other Microsoft services, Storm-0324 targeted organizations with embedded links to fake login pages, aiming to steal user credentials.
October 2023: In October 2023, a RAMP ransomware post detailed how to exploit stolen Primary Refresh Tokens (PRTs) to infiltrate Microsoft Teams data. By extracting credentials from Teams messages, attackers gained lateral movement capabilities, using compromised accounts to send internal phishing messages.
That same month, DarkGate expanded its tactics to target Teams as an entry point. Partnering with BlackBasta, DarkGate delivered payloads via Teams alongside its usual PDF methods, embedding additional Indicators of Compromise (IOCs) that made malicious activities harder for victims to detect.
While these cases may not be directly related, the timing and tactics suggest that DarkGate’s targeting of Teams likely stems from its alliance with BlackBasta. It’s also possible that BlackBasta’s use of Teams-centric social engineering was influenced by Nobelium’s earlier campaigns.
Among post-Conti groups, BlackBasta stands out as the most centralized and disciplined. This structure makes them a strong candidate for potential collaboration with Russian state hacking groups. Unlike other groups who often rely on opportunistic hits, BlackBasta has continued to conduct long-planned, targeted attacks on European and U.S. critical infrastructure and the military-industrial complex, showing a level of coordination and intent beyond mere chance.
The nature of BlackBasta’s victimology actively supports this theory. Based on the active incidences and internal adversarial data (not the public data from the group’s blog, which cannot be considered valid victimology data), RedSense observed an unprecedentedly high level of focused and preemptive targeting by the group in 2024, compared to an increasing landscape of ransomware groups relying on opportunistic approaches.
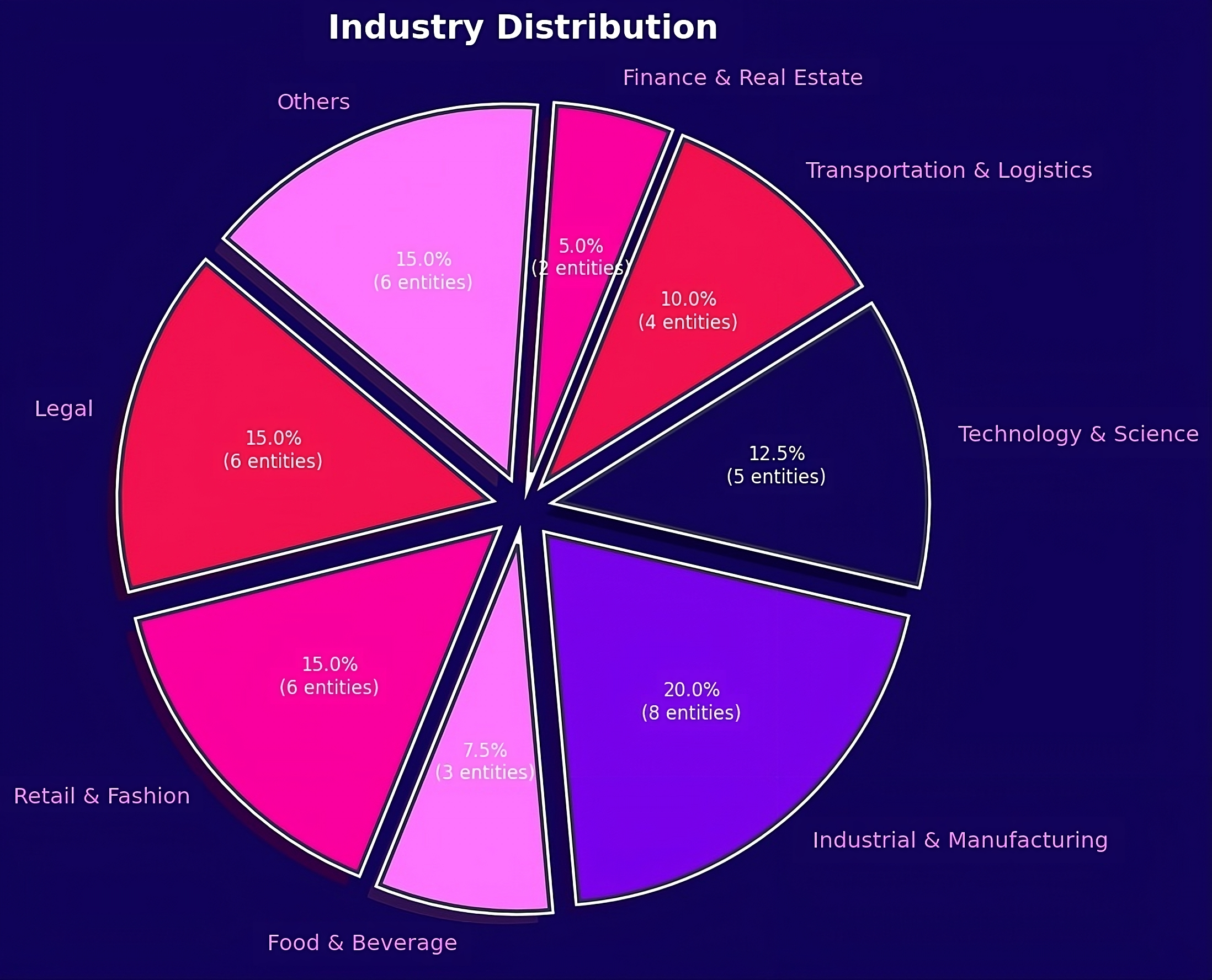
Infographic depicting BlackBasta’s industry distribution for attacks from 2022 to 2024. Note how BlackBasta’s victimology prioritizes legal, tech, and manufacturing sectors. This is due to their precise targeting of the Western military-industrial complex.
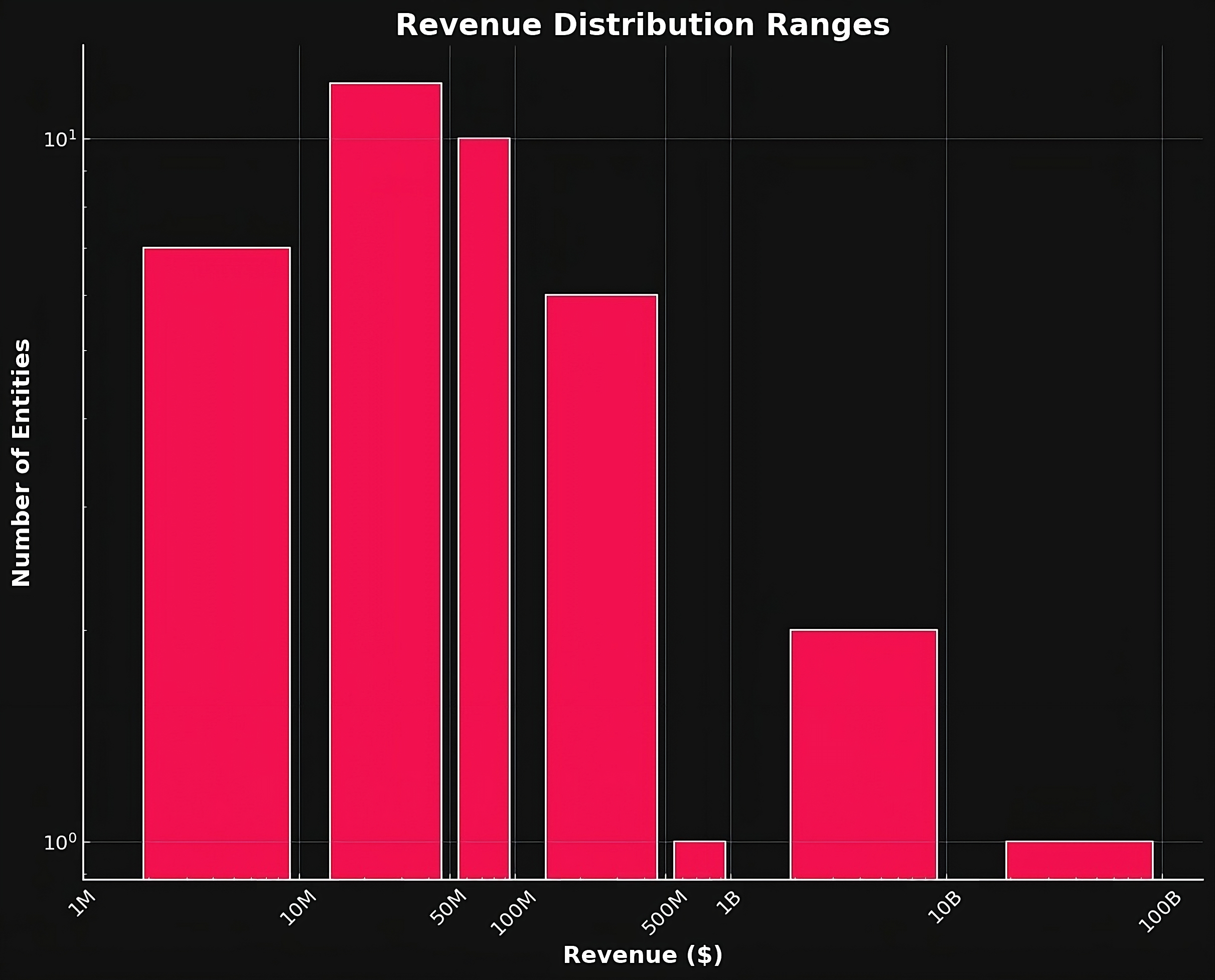
Infographic depicting BlackBasta’s revenue distribution for its attacks from 2022 to 2024. Note the unprecedented percentage of victim companies with revenue over $100 million USD, even up to $3 billion USD. This is uncommon for a significant portion of ransomware groups whose entire victimology usually falls under $10 million USD in annual revenue.*
Post-Conti Influence
Another significant influence on BlackBasta’s dissemination tactics comes from the broader post-Conti community, particularly the Royal-BlackSuit malware lab, which BlackBasta likely contributed to.
Among its many 2023-2024 projects, several included impersonation tactics that involved posing as reputable entities to deceive targets into downloading malware or granting access, including:
- Citrix Impersonation: Royal created a fake Citrix workspace site, tricking users into downloading malware disguised as legitimate software.
- Udemy Impersonation: Victims receive fake invoices from “Udemy,” with a support number that connects them to Royal’s operators, who direct them to download malicious files.
- Adobe Acrobat Impersonation: Royal distributed PDF attachments via email, which used ActiveX objects to coerce victims into downloading various botnets.
Infographics depicting numerous malware that were identified within Royal/BlackSuit’s joint malware lab. [Source: RedSense]
An in-depth whitepaper covering the Royal-BlackSuit malware lab is available via the RedSense intel portal.
In December 2023, Microsoft outlined the TTPs of Storm-1113 campaigns
, which exploited Microsoft’s App Installer to deploy stealers like IcedID, Gozi, Redline, Batloader, and, notably, Lumma Stealer. This arsenal mirrored the tools found in Royal’s malware lab, hinting at Royal’s possible involvement. The resemblance carried into a June 2024 CrowdStrike impersonation campaign which also centered around Lumma deployment, further suggesting Royal’s activity in both instances.
On July 23, 2024, CrowdStrike uncovered a phishing campaign using a fake domain, crowdstrike-office365[.]com, which impersonated CrowdStrike to deliver Lumma Stealer malware. This malware was distributed via an MSI file disguised as a Falcon sensor update. CrowdStrike stated:
“The same C2 domain identified in this activity was observed in a recent widespread opportunistic spam flood and voice phishing (vishing) campaign in June 2024; in that campaign, the threat actor sent numerous spam emails and conducted follow-up phone calls masquerading as a “helpdesk” operator via Microsoft Teams.”
As seen throughout this blog, this pattern is almost identical to the recent BlackBasta social engineering.
In other words, a campaign that utilized malicious MSI files(potentially known to BlackBasta via the malware lab) evolved into a direct impersonation of CrowdStrike in June 2024. By July 2024, it gained a social engineering component nearly identical to BlackBasta’s current tactics (i.e., MS Teams impersonation targeting).
Conclusion
BlackBasta’s evolution in malware dissemination shows a peculiar shift from a purely botnet-reliant approach to a hybrid model that integrates social engineering. By 2024, BlackBasta’s dissemination model increasingly mirrored the advanced social engineering tactics seen even across nation-state APTs. This evolution shows BlackBasta’s deliberate progression from opportunistic attacks to strategic, long-term planning. This evolution positions BlackBasta as a model for future post-Conti ransomware operations, effectively blending technical and social tactics to sustain relevance and resilience in a challenging environment disrupted by LEA takedowns. It hints at an ability to leverage both internal resources and external influences (malware lab) to adapt and endure.