Introduction
It has been almost a year since international law enforcement took down LockBit — a group once referred to as “the most prolific ransomware.” In reality, LockBit has never been the most prolific, and should instead be referred to as the “most talkative ransomware.”
This is why, a year after the takedown, we are looking at LockBit in the context of the larger ecosystem. While the group as an organized body is likely dead, its talent has moved to other groups, and its intellectually dysfunctional leadership is facing Russian imprisonment, the changes that LockBit brought to the threat landscape are still present. Specifically:
- LockBit builder, which enables anyone to create a derivative for the LockBit locker for individual attacks.
- Weaponization of false data breach claims, which are used for intimidation purposes.
- Deceptive practices, such as inflating the number of its victims by listing third-party companies without direct breaches while presenting a false narrative of widespread success
- Involvement in cryptocurrency-related activities, including adversarial mining and laundering.
- Utilizing other groups to expand its attack surfaces.
- Use of ExMatter to scan for and exfiltrate files or read mapped network drives and leveraging of Inter-process Communication (IPC) for lateral movement.
Judging by chatter within the threat landscape, other top-tier actors, while agreeing on general contempt for LockBit, were and are closely monitoring its previous successes and current demise. They are learning the TTPs above and will or are using them for their collectives.
In this blog, we will review the TTPs introduced by LockBit which are persistent even after a year after the takedown and are present in the larger ecosystem.
NOTE: This blog covers LockBit as an organized ransomware-as-a-service group. At this point, numerous individual actors are using the LockBit locker or its builder-based derivatives for ransomware attacks without any connections to LockBit as an organization.
For our review of the evolutionary journey of LockBit and its allies, please read RedSense’s public blog “LockBit Story: A Three-Year Investigative Journey
.” Here, we followed how LockBit has evolved into a leading Ransomware-as-a-Service (RaaS) operation, tracing the group’s development and its alliances, most notably with the Conti derivative group Zeon.
Screenshot of the front page of the law enforcement-controlled website formerly used by LockBit to post target data, captured Oct. 1, 2024, after the announcement of additional actions against LockBit. [Source]
Threat Actor Profile
Threat Actor: LockBit
Malware Type: Ransomware
Status: CURRENTLY NON-OPERATIONAL (as a group not as a threat)
Origin: Eastern Europe / Original Netherlands (claim)
Functionality:
- RaaS
- Data encryption
- Data exfiltration
- DDoS
- Threats of physical violence
MITRE ATT&CK Framework:
- T1562.001 - Impair defenses: disable or modify tools
- T1070.001 - Indicator removal on host: clear Windows Event Logs
- T1041 - Exfiltration Over C2 Channel
- T1486 - Data encrypted for impact
- T1489 - Service stop
- T1490 - Inhibit System Recovery
- T1190: Exploit Public-Facing Application
- T1547: Boot or Logon Autostart Execution
- T1003: OS Credential Dumping
- T1083: File and Directory Discovery
Distribution:
- Zeon (Ghost Group)
- Independent Threat Actors
- Use of other threat group lockers (previous examples include HIVE, HelloKitty, ALPHV, and Royal/BlackSuit)
Capability Level: LOW
Decrypter: Not Released
Group Timeline
As a quick recap of our blog on the evolution of LockBit
, here is a timeline of how LockBit developed from 2019 to 2024. Below that is a more detailed step-by-step explanation of their history.

LockBit Step-by-Step History
September 2019: LockBit, initially called ABCD ransomware, first emerges as a collaboration of actors from the underground forum exploit[.]in. The LockBit locker gains recognition for its efficient encryption and well-designed admin panel.
January 2020: ABCD ransomware is renamed to LockBit on underground forums.
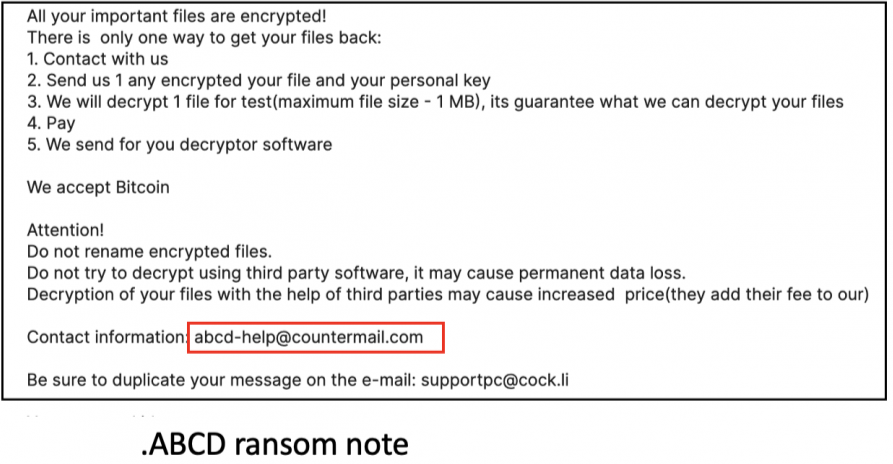
Screenshot of the rebranded LockBit ransom note (bottom) vs the original ABCD ransom note (top). [Source]
Summer 2021: LockBit 2.0 launches, marking a new phase for the group. The group gains attention for its attack on Accenture, possibly aided by an insider. During this period, LockBit also begins engaging with former Avaddon and REvil pentesters.
At the same time, LockBit becomes more engaged with the media, particularly security journalism, first Russian-speaking and then English-speaking, actively using the social media hype to amplify the damages of their victim-shaming.
Fall 2021: LockBit makes its first strategic connections with Conti’s leadership, gaining access to Conti’s allies, including HIVE, Avos, HelloKitty, and BlackCat.
June 2022: LockBit 3.0 is introduced, notable for implementing a “bug bounty” program with financial incentives.
Fall 2022: A builder for LockBit 3.0 is leaked, allowing anyone to create customized versions. Groups like the NATIONAL HAZARD AGENCY, GetLucky, and Bl00dy adopt these builders.
Fall 2022: Following Conti’s collapse, LockBit forms its first major alliance with Conti’s Team2 (Royal/BlackSuit) and Team1 (Zeon), leading to a surge in high-profile attacks.
November 2022: RedSense analysts uncover LockBit inflating its victim numbers by listing third-party companies affected by its actual victims.
January 2023: LockBit strengthens its relationship with ex-Conti members, creating “LockBit Green,” a locker tailored for ex-Conti pentesters.
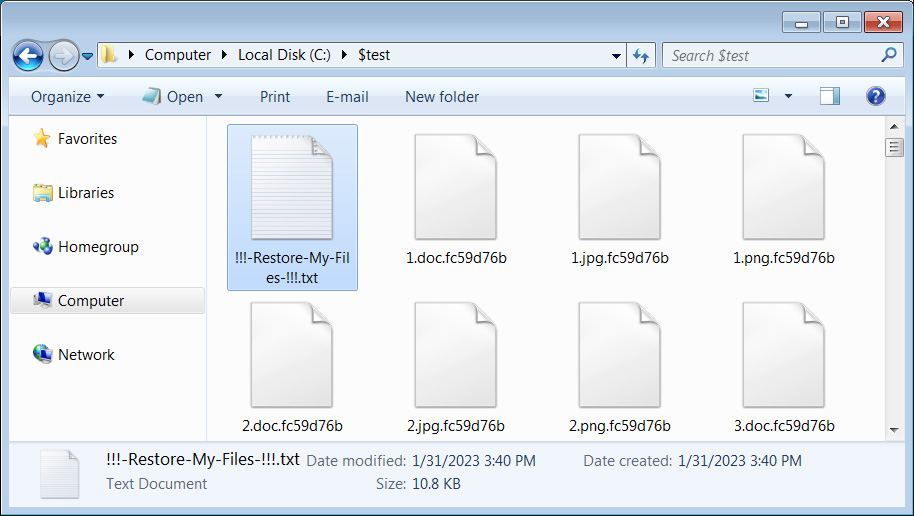
Example of the “randomized” file extensions used for LockBit Green, rather than the traditional .lockbit extension used in LockBit 3.0 attacks. [Source]
Spring 2023: The Conti-LockBit alliance expands with connections to 3AM and BlackCat through Zeon. On April 15, 2023, LockBit began targeting Apple devices with a MacOS variant of its payload.
Summer 2023: After Royal rebrands as BlackSuit, LockBit shifts most of its large-scale operations to Zeon (Conti1). On June 14, 2023, CISA released a joint cybersecurity advisory on LockBit ransomware. [Source]
November 2023: LockBit exploits the “Citrix Bleed” vulnerability, launching an attack on Boeing and claiming to steal over 50GB of data.
January 2024: RedSense confirms that Zeon operates autonomously as a “ghost group” for LockBit and Akira, handling large-scale threat operations and providing key services like call centers and high-end accesses.
February 2024: On February 19, 2024, LockBit’s official shame blog is taken down by law enforcement. By February 26, 2024, the group reuploads a version of the blog, mixing older data with new accesses achieved by Zeon.
May 2024: LockBit briefly resurfaces, claiming to be the most active ransomware group, though this resurgence was largely superficial, hiding internal turmoil. By this time, LockBit’s affiliate count had significantly dropped.
October 2024: Further arrests are made, including key members of LockBit’s infrastructure. The group’s reputation and affiliate network continue to dwindle as newer ransomware groups like Akira and RansomHub attract LockBit’s former affiliates.
Current Lockbit Status

Screenshot of the customization section of the LockBit builder [Source]
At this point, LockBit as a syndicate has been seriously damaged. The core pentesting team mostly moved to Akira, Play, and BlackSuit; the blog, which was critical for victim shaming, is down, and the social media hype related to LockBit’s admin and weaponized for intensifying this said victim shaming has wound down.
However, a critical event took place that kept LockBit as one of the top threats. In September 2022, a builder for LockBit 3.0 was leaked, allowing various groups to create customized versions of the ransomware. This led to hundreds of unique LockBit variants being detected, with Kaspersky reporting 396 telemetry hits, 312 of which were created using the leaked builders. Notably, 77 of these variants did not reference LockBit in their communications.
Soon after the leak, Kaspersky discovered a breach using a LockBit variant named “Trojan.Win32.Inject.aokvy,” which encrypted critical systems. The ransom note in this attack, however, was different and was signed by the group “NATIONAL HAZARD AGENCY.” Other ransomware groups, such as Bl00dy and GetLucky, were also found to be utilizing the leaked LockBit builders for their operations, each using their own custom ransom notes.
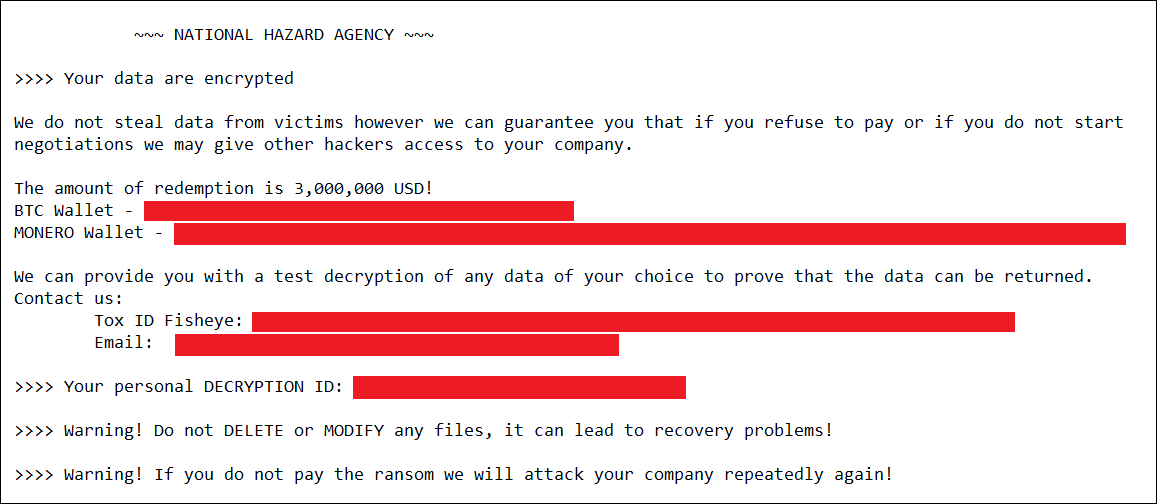
Screenshot of the “NATIONAL HAZARD AGENCY” ransomware note found with “Trojan.Win32.Inject.aokvy”. [Source]
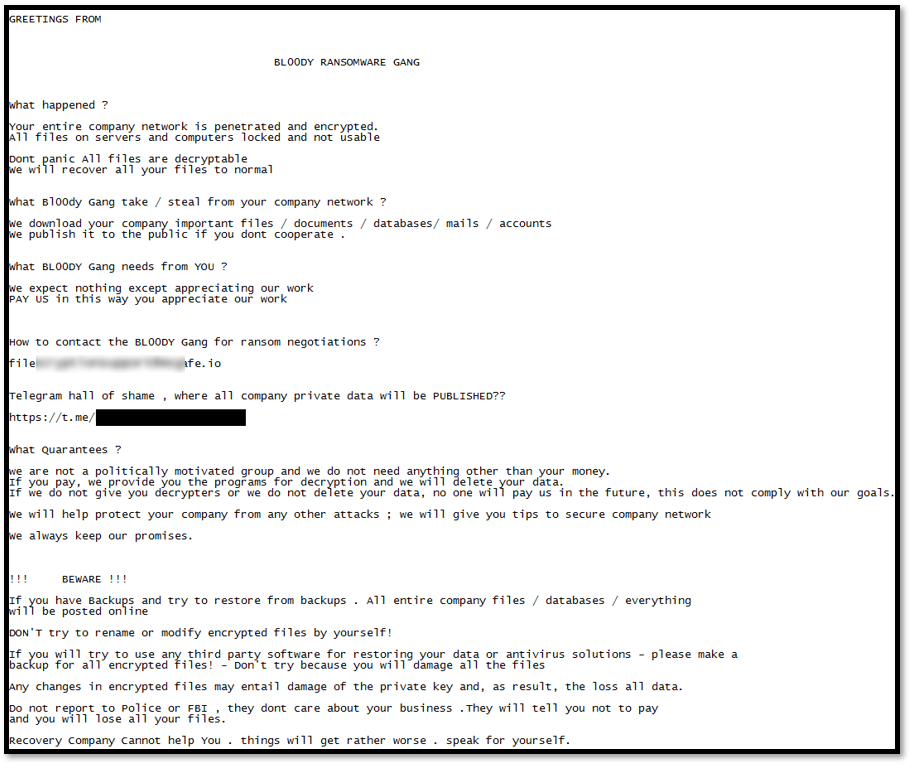
Screenshot of the Bl00dy ransomware note found with a version of the exfiltrated LockBit builder during an attack. [Source]
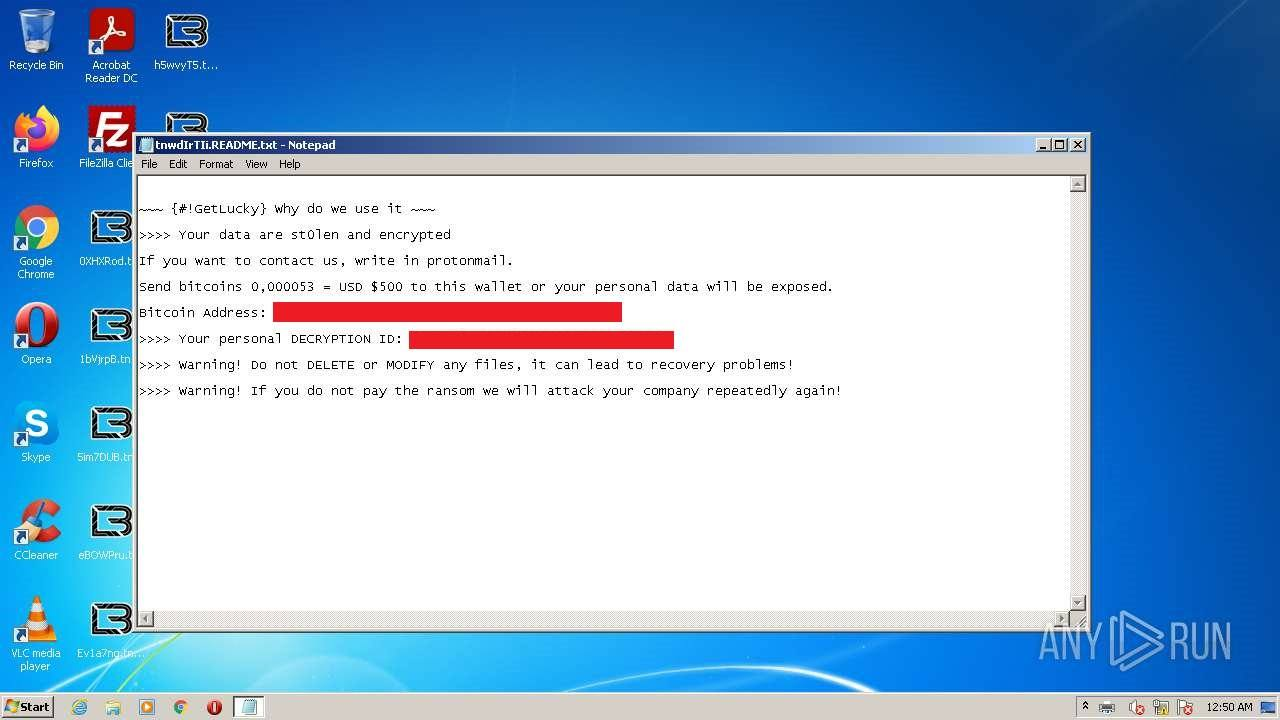
Screenshot of the GetLucky ransomware note found with a version of the exfiltrated LockBit builder during an attack. [Source]
This way, while LockBit as a syndicate is mostly dismantled, LockBit as a locker has been used by hundreds of unrelated hackers and actors threatening thousands of companies on a scale that would be unachievable for LockBit as a group.
Specifically, it has been discovered
that the LockBit 3.0 ransomware builder is being used not only for large-scale dissemination but also to create highly customized ransomware for targeted attacks.
In a Spring 2024 incident response case, actors leveraged the builder to modify ransomware payload to suit specific network environments. This is because, unlike pre-built ransomware kits, the LockBit builder allows attackers to tailor every aspect of the killchain. Most importantly, it was concluded that the files encrypted with a derivative LockBit builder could not be decrypted with existing decryption tools geared to LockBit after its takedown, because the independent groups and actors using the builder did not share their private keys with the LockBit syndicate.
Operational Details: TTPs, Killchain & IOCs
Killchain Nuances & ExMatter
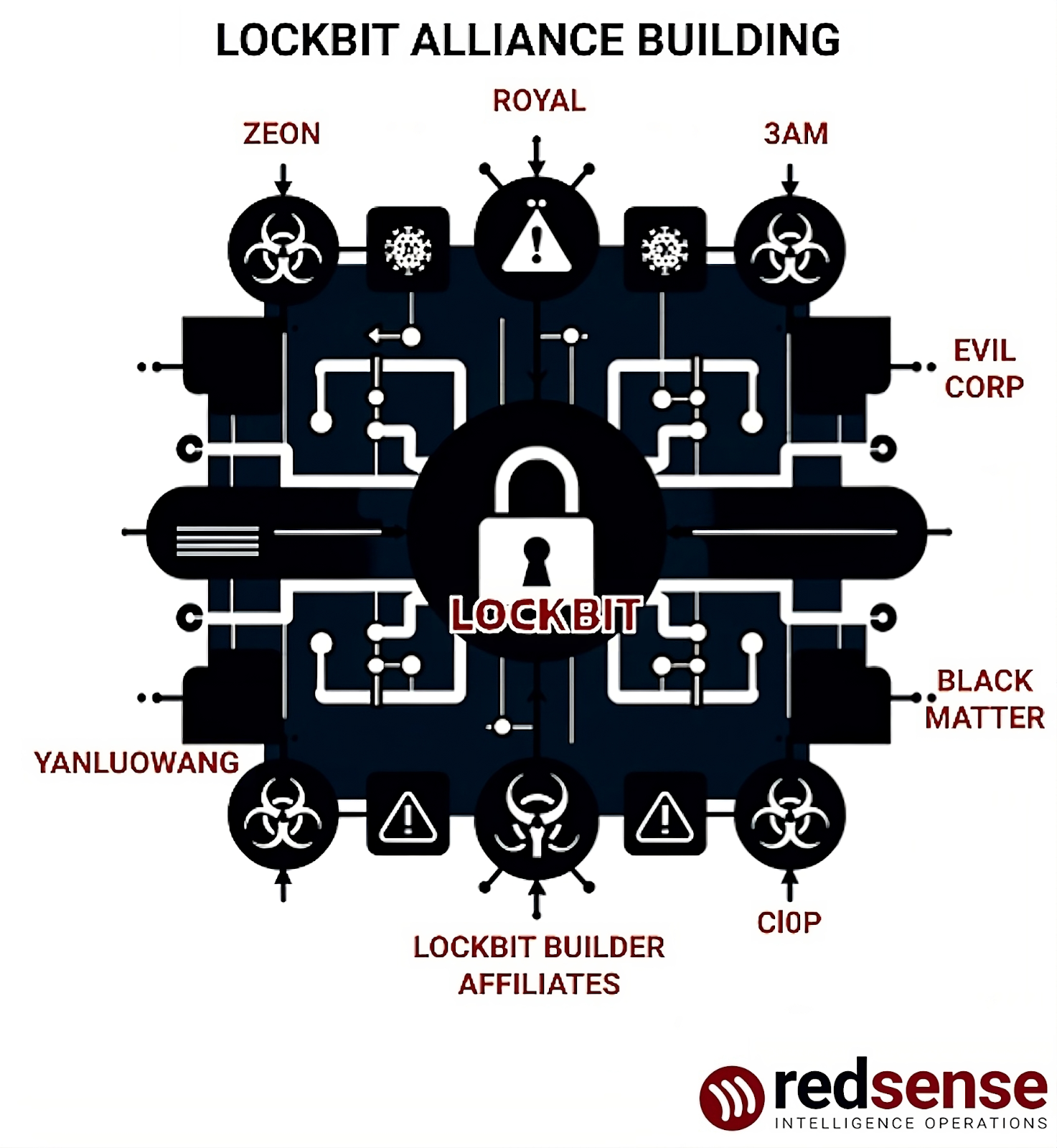
LockBit itself has limited capabilities, and was relying heavily on the post-Conti group Zeon for high-level access. Zeon provided services such as call centers, spam, and initial access, enabling LockBit to continue its operations. LockBit supplies its own locker, blog, negotiations, and data publishing but outsources complex tasks requiring pentesting skills to Zeon. Zeon primarily operates as a “ghost group,” supporting external ransomware groups in a similar capacity.
The most common killchain for LockBit 3.0-Zeon operations has traditionally been the following:
Initial Access | LockBit actors gain initial access to a system primarily via compromised servers or RDP accounts from affiliates. The group has also been known to utilize spam mail and brute force tactics to obtain RDP and VPN credentials. |
Privilege Escalation & Lateral Movement | Once initial access is gained, LockBit has been known to use UAC bypass techniques, as well as utilizing tools such as Mimikatz, Cobalt Strike and PSExec in order to move laterally and gain admin access. |
Defense Evasion, Discovery | Tools have been observed in LockBit attacks that are used to disable security protections, such as GMER, PC Hunter, and Process Hacker. |
Encryption/Exfiltration | At this point in the attack, LockBit will begin exfiltrating desired data from target devices and will seek to access the network domain controller and lock target systems for ransom purposes. |
ExMatter, a .NET binary used by LockBit, consistently appeared during execution phases in RedSense’s investigations, although direct C2 activity wasn’t always confirmed. ExMatter infiltrates victim environments, scans for files, and exfiltrates them to a WebDAV server via HTTP. As of early 2024, ExMatter remains LockBit’s preferred precursor for data exfiltration.
Based on past operational precedent as well as RedSense’s current campaign visibility, ExMatter remains the LockBit precursor of choice.
Significant upgrades to ExMatter were observed in early 2024. The January 2024 variant (SMSAgent.exe, SHA1: 7c67976bfc3ef3c673d5cabc60b7f6fbe0ab19dc) improved lateral movement by reading mapped network drives from the Registry and leveraging Inter-process communication (IPC) to execute across network shares remotely.
Considering that Zeon has merged with Akira (and to a lesser extent Play), RedSense assesses with a high level of certainty that the aforementioned TTPs will be used by these groups.
IABs
From mid-2023 to early 2024, LockBit-affiliated IABs exploited vulnerabilities in critical tech stacks (e.g., Citrix Bleed, Ivanti) to secure fresh access flow. LockBit has been observed leveraging these vulnerabilities with rapid operational turnaround, sometimes initiating exfiltration within 24 hours of initial access.
Compromised credentials also remain a common initial access vector, with groups like Scattered Spider exploiting credentials and using social engineering to bypass MFA, adding another layer to LockBit’s initial attack strategies.
Active Incident Example 1
Host | Proxy Domain
(if applicable) | Session IP/Port Activity | Amount of Data Transferred | Notes |
Digital Ocean | N/A | 198.199.74.168 | N/A | IAB device (likely RDP tunnel/phishing) |
Digital Ocean | N/A | 198.199.82.43 | N/A | active LockBit exfiltration |
Digital Ocean | N/A | 159.89.236.37 | N/A | IAB device (likely RDP tunnel/phishing) |
Digital Ocean | N/A | 104.248.23.242 | N/A | active LockBit exfiltration |
Active Incident Example 2
Host | Proxy Domain (if applicable) | Session IP/Port Activity | Amount of Data Transferred |
Digital Ocean | realmigrator[.]com | 159.223.251.165 | 1 GB |
LUMINATI | N/A | 89.203.223.42 | 1 GB |
Although the IP recipients in question have not been specifically linked to LockBit activity in the past, there are a number of red flags that indicate threat actor activity in regard to these two telemetry findings:
REDSENSE™ RED FLAGS🚩
- Large data transfers to an unknown third-party host device are often illegitimate activity, as there are few instances in which this occurs through official protocol.
- Unusual activity which occurs during the timeframe before the victim is proclaimed as a successful attack on LockBit’s blog, indicating possible data theft.
- When the destination IP is part of known LockBit infrastructure or is a known proxy endpoint (further information regarding recent adversarial use of proxies can be found below).
Note that while LockBit is (mostly) down, these IABs and their tactics are still present.
IOCs
RedSense recommends that the following indicators of interest be shared downstream for the earliest possible detection (prior to exfiltration complete and locking) where possible.
- 198.199.74.168:22
- 198.199.74.168:80
- 198.199.74.168:443
- 198.199.82.43:22
- 198.199.82.43:25
- 198.199.82.43:53
- 198.199.82.43:80
- 198.199.82.43:443
- 198.199.82.43:3389
- 198.199.82.43:5432
- 104.248.23.242:22
- 104.248.23.242:25
- 104.248.23.242:53
- 104.248.23.242:80
- 104.248.23.242:443
- 104.248.23.242:3389
- 104.248.23.242:5432
- 159.89.236.37:22
- 159.89.236.37:25
- 159.89.236.37:53
- 159.89.236.37:80
- 159.89.236.37:443
- 159.89.236.37:3389
- 159.89.236.37:5432
TTPs
REMOTE SERVICES: SSH
By logging into a legitimate service provider or compromised device, attackers gain a layer of obfuscation while performing actions such as directory traversal or data exfiltration. Many of these servers run outdated versions of OpenSSH, NGINX, and FTP, which have known vulnerabilities, providing attackers with further opportunities for exploitation.
PROXY: DOMAIN FRONTING
Exploiting routing schemes in Content Delivery Networks (CDNs) and services hosting multiple domains to obfuscate the true destination of HTTPS traffic enables threat actors to mask their activities and evade detection. Recent RedSense telemetry shows a growing use of proxy and anonymization services in victim environments. LockBit and Royal increasingly rely on proxies and redirects to obscure their movements further and avoid network-based defenses.
APPLICATION LAYER PROTOCOL: DNS
/ PROTOCOL TUNNELING
LockBit utilizes the Domain Name System (DNS) application layer protocol to evade detection by blending their communications with legitimate traffic. Commands and their responses are often embedded within DNS traffic between client and server. When using DNS over HTTPS (DoH), these queries and responses are encrypted, further obfuscating activity by utilizing HTTP or HTTP/2 protocols.
Additionally, they employ protocol tunneling to conceal network communications within another protocol, bypassing detection and gaining access to restricted systems. Tools like Cobalt Strike and Brute Ratel C4 commonly generate traffic over HTTPS, further complicating detection efforts.
Post-Breach Exploitation
In August 2021, underground forum members noticed discrepancies in the LockBit’s shame blog, pointing out that many companies listed as victims had no actual data posted. These “filler” victims appeared to be named without any corresponding data leaks, seemingly included to inflate LockBit’s reputation and make the group appear more prolific than it was.
Source: (Russian-language underground forums), highlighting the alleged discrepancy in LockBit’s supposed successes.
In November 2022, RedSense analysts accessed adversarial communications revealing that LockBit had inflated its reported victim numbers on its underground shame blog. Despite claiming a high volume of successful exfiltrations, RedSense discovered that many “victims” listed were third-party companies whose data was found within the systems of actual victims. This tactic allowed LockBit to falsely present these companies as direct targets of its operations.
Misinformation, deception, deliberate message, and intelligence poisoning have been very typical tactics for LockBit since 2021. They have actively used social media profiles and interviews with security researchers to re-weaponize some of HUMINT operations, which were aimed against LockBit to poison and misinform the security community by providing deliberately false information during HUMINT engagements.
RedSense confirmed that LockBit had added an unprecedented number of supposed victims, with 271 entities listed on October 30, 2022, alone, indicating an ongoing pattern of exageration to bolster the group’s reputation.
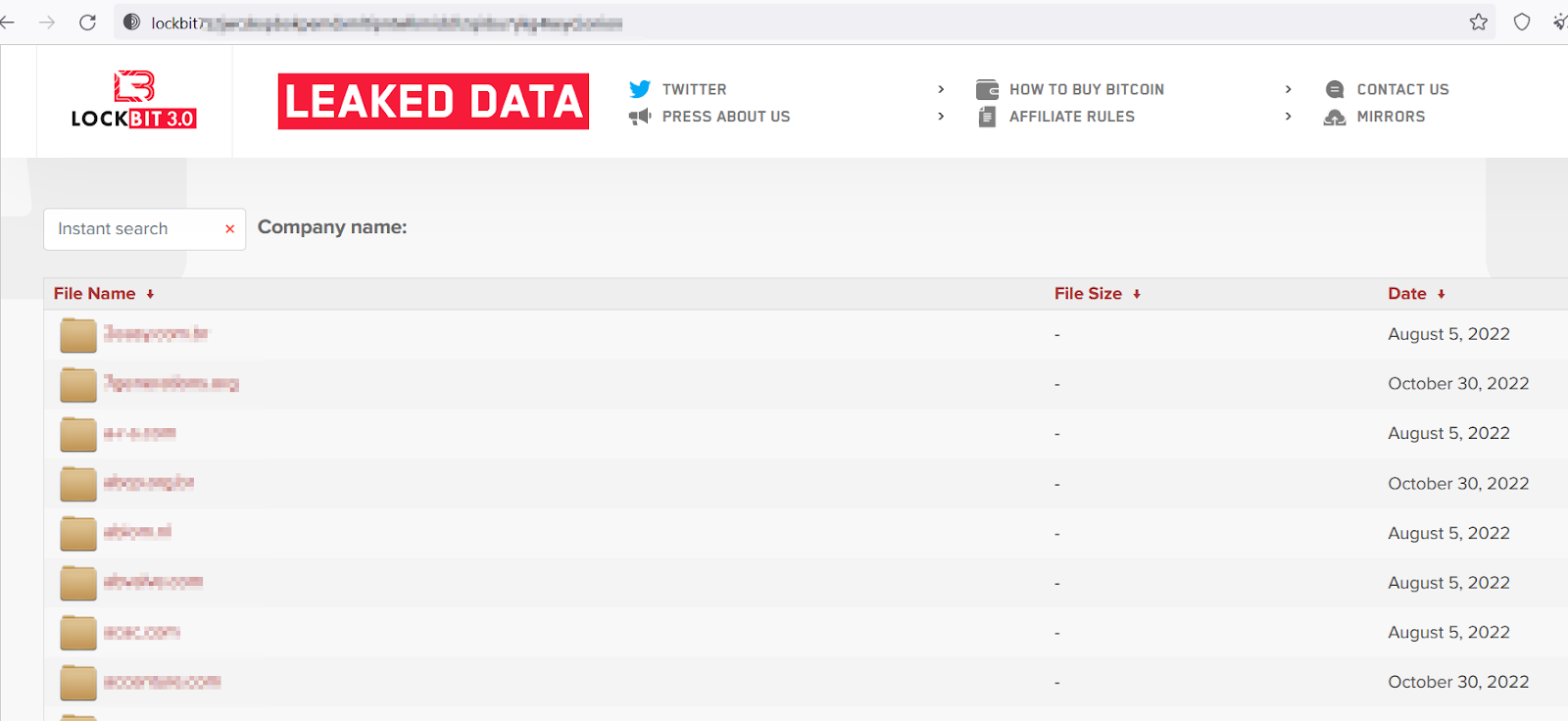
Screenshot of the homepage of LockBit 3.0’s proprietary underground shame blog.
Upon analyzing the exfiltrated data posted on LockBit’s website, it was revealed that many supposed “direct breach” victims were actually companies involved in third-party data exposures. LockBit had reposted these files to present them as results of distinct system breaches falsely. Essentially, the group found files related to other companies within compromised data and then claimed them as separate infiltrations.
NOTE: This tactic has been used by Akira in 2024.
For instance, directories for companies like the French technology firm Thales Group
were posted as though they had been directly breached. Still, they were later identified as part of third-party exposures.
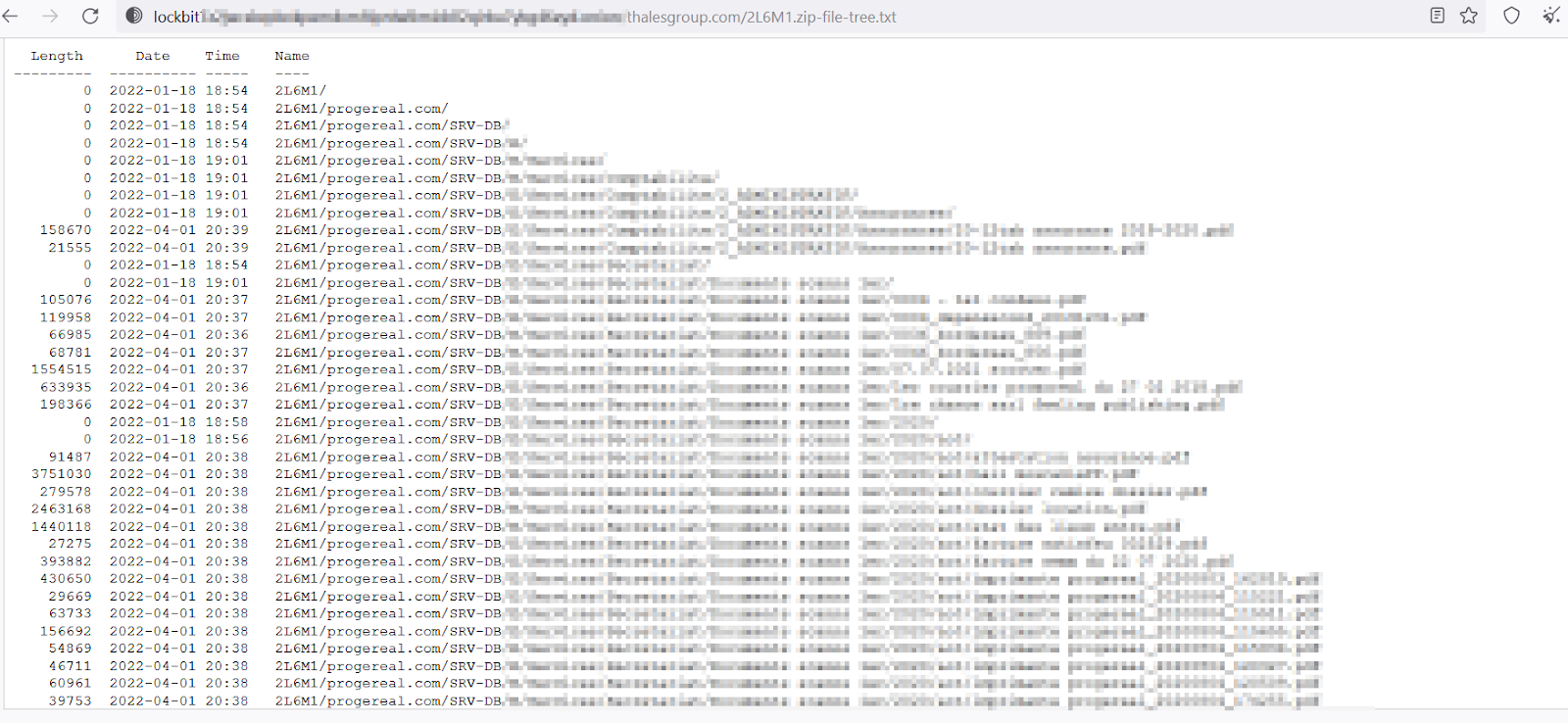
Screenshot from LockBit Victim File Directory posted on the group’s shame site for the company Thales Group.
And the second was posted under the name of French real estate company Progereal
on October 30th:
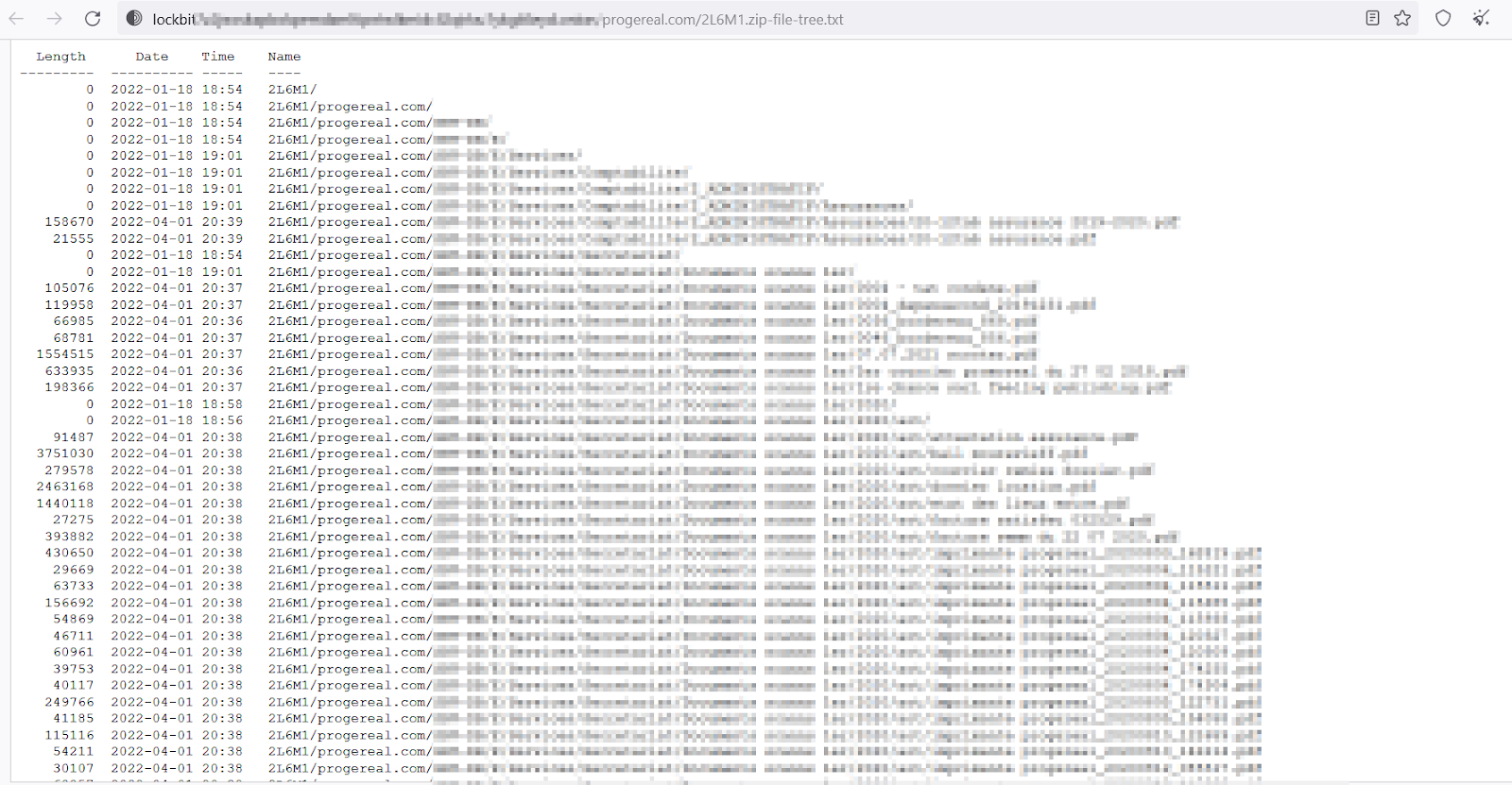
Screenshot from LockBit Victim File Directory posted on the group’s shame site for the company Progereal.
A cursory survey of the file directories and associated data shows that LockBit appears to have merely taken Progereal-related files from the systems of Thales Group and reposted them to make it appear as though Progereal’s systems were breached separately.
Lastly, in a finding reminiscent of observations of the LockBit 2.0 shame blog, some victim listings (such as the Comune di Villafranca di Verona
in Italy, listed on August 05) merely contained empty file directories with no associated data within.
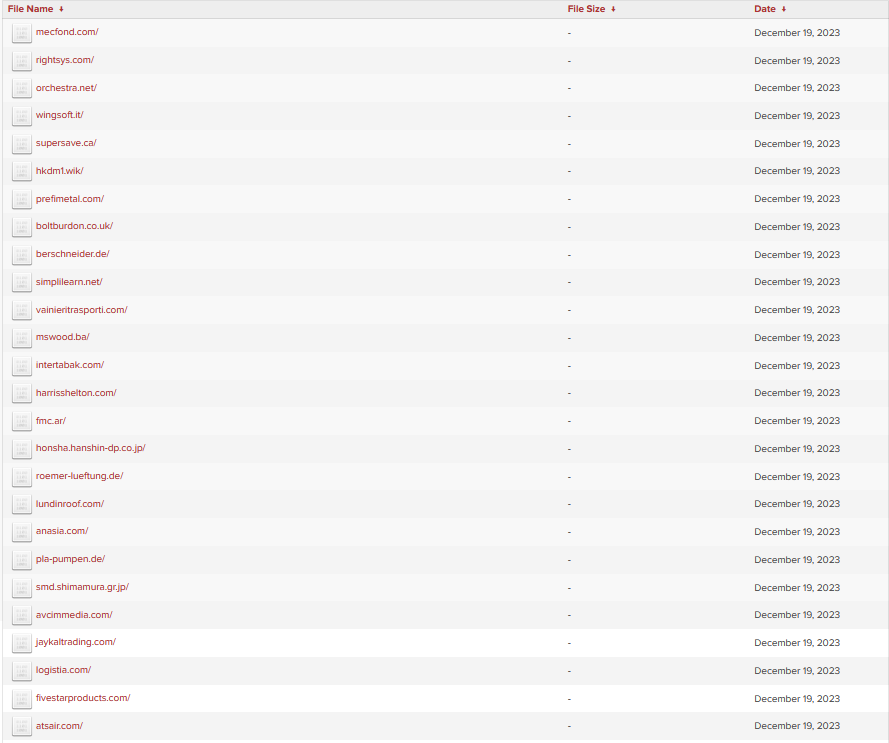
Screenshot from LockBit’s proprietary shame blog “leaks collections” as of December 19, 2023.
LockBit regularly posts numerous victims in a single day. This mass-publishing, often based on a technicality or outright misrepresentation, misleads viewers who see the volume of high-profile names but don’t verify the actual data. This tactic allows LockBit to claim large-scale attack success and gain publicity without executing multiple attacks.
CRYPTOCURRENCY & LOCKBIT
In 2022, a group Yanluowang experienced a significant leak that exposed around 2,700 private Matrix messages, made publicly available via the now defunct @yanluowangleaks Twitter account, along with a breach of the group’s shame site.
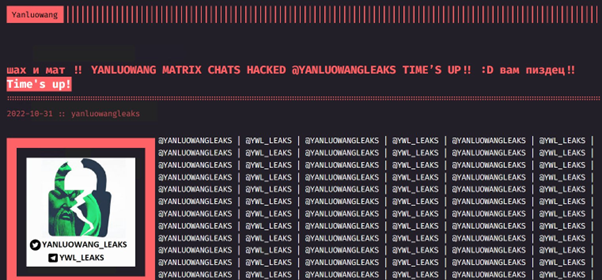
Screenshot from the hacked Yanluowang shame site. The “Time’s up” is a reference to the phrase used by the group themselves when posting data of their victims after failing to receive payment.
Among these messages, an exchange from January 2022 discussed methods for discreetly converting Bitcoin to cash. “exchanging via (LockBit) to (a QR code).” One member mentioned using LockBit’s services at a physical location in Russia, referencing the crypto exchange platform BestChange
.
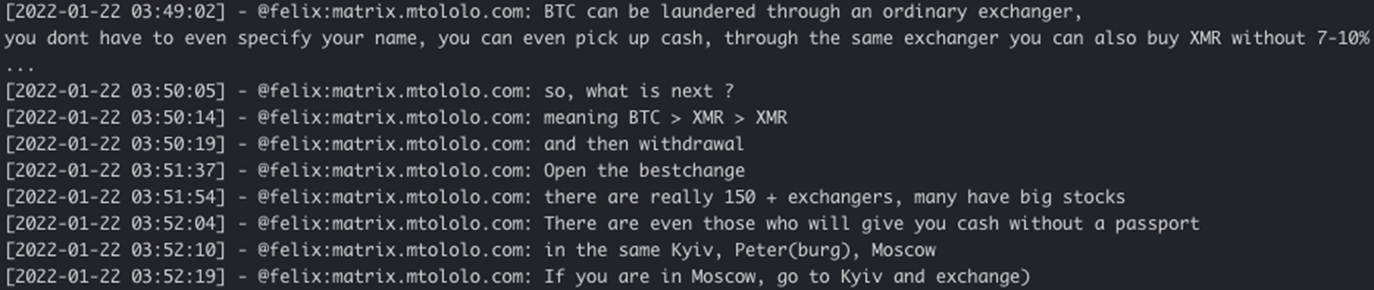
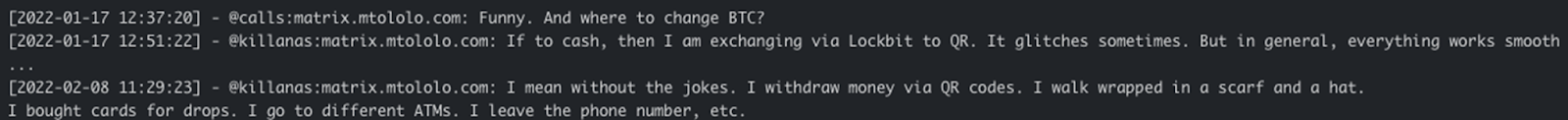
Screenshots of leaked Yanluowang Matrix chat messages. In the messages, two threat actors discuss potential processes for converting Bitcoin to cash using a physical exchange location in Russia, with both QR codes and the cryptocurrency Monero (XMR) functioning as “middlemen".
The Bitcoin exchange(s) attacked by LockBit, which are being referenced above, may be referring to the group’s February 2022 ransomware attack on PayBito
, a “white label crypto exchange software.” During this attack, threat actors claimed to successfully exfiltrate “100k Users in DB. Customers from USA/WorldWide personal data, mail/hash…Admins personal data, admin emails, and hashes.”
The stolen data, although leveraged for ransom due to the potential of identity or currency theft concerns for PayBito’s users and admins, was most likely not taken for crypto exchange purposes. A ransomware operation regarding an exchange would not benefit from using ransomware that can convert BTC to currency when it is much more effective to merely steal crypto users’ data and transfer their (decentralized and hard to track) cryptocurrency away from them.
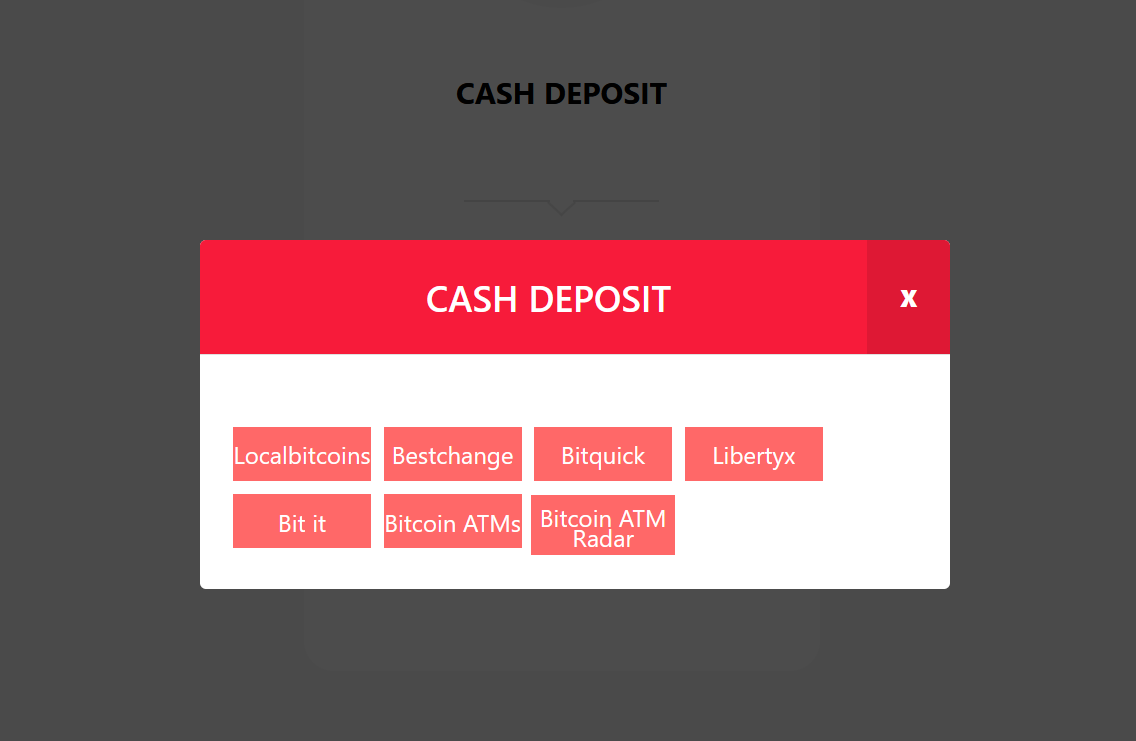
Screenshot from LockBit’s official dataleak site showing different methods of exchanging cash for BTC, one of which (Bestchange) was discussed between Yanluowang threat actors in leaked Matrix chats.
In addition, In 2023, RedSense observed DNS requests linked to ALPHV (associated with LockBit via Zeon) that suggested adversarial cryptocurrency mining activities. These outbound DNS lookups to a common mining pool indicated connections to crypto mining by related groups.
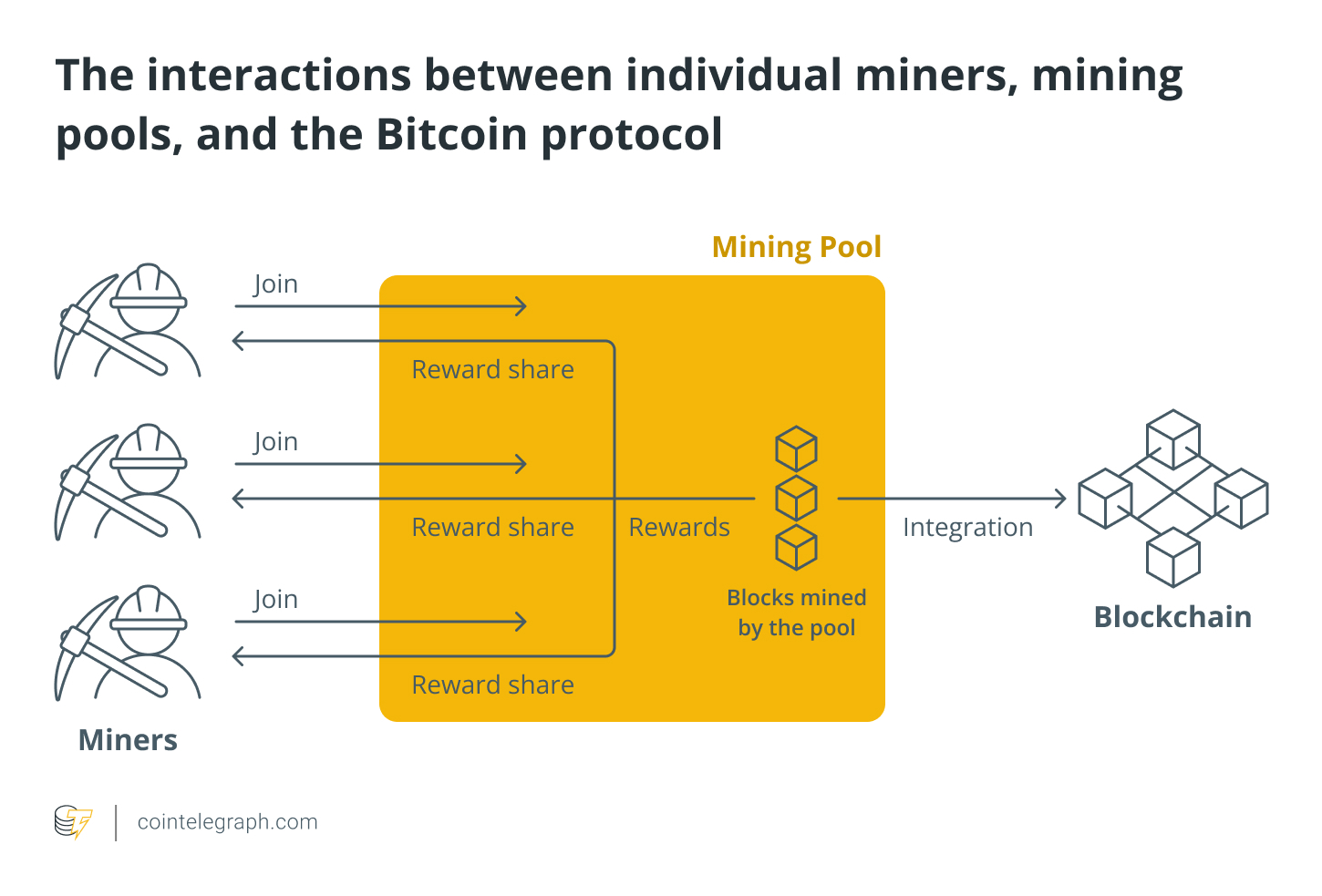
Illustration of the relationship between crypto miners, mining pools, and the blockchain [Source].
Conclusion
LockBit has been a part of the ransomware ecosystem for over four years, and this time, they were able to change it significantly.
The most critical impact that set the LockBit legacy was the release of the builder that is, to this day, enabling tens, if not hundreds, of individual actors to deploy ransomware on their own.
The other change was that LockBit “taught” other groups how to treat the stolen data. At the beginning of the ransomware spike in 2019, most groups actually cared about their reputation and aimed to keep their promises and stand by their word. LockBit, with its campaigns of upfront disinformation and active use of social media, proved that even if you make false claims, you can still get enough attention to be paid.