This is a summary review taken from our year-long project: The Ransomware APT White Paper—a 200-page cumulative research paper covering our five-year insights (2019-2024) into ten top-tier ransomware groups serving as the backbone of today’s ransomware economy. The complete, unabbreviated white paper is available to all RedSense Advantage and RedSense-as-a-Service subscribers.
This current list of trends and interconnectivity findings for the past year covers long-term observations RedSense has made regarding the ever-changing threat landscape. These observations were made by analyzing numerous 2023 threat findings and discoveries and include references to case-studies that were reported on by RedSense throughout the year.
This trend review will be presented in addition to RedSense’s in-depth, up-to-the-minute adversarial threat profiles on top ransomware groups, as well as a detailed intelligence summary of our findings. Look out for what’s around the corner in 2024!
2023 Intel Trends
1. “Ghost Groups” & Their Impact
The main trend that has completely reshaped the threat landscape in 2023 is “outsourcing” or use of “ghost groups” for threat operations. These groups (named for the practice of “ghostwriting”) operate behind the scenes, but are given a wide platform for their demands by more public-facing groups. In turn, the ghost group’s capabilities elevate their lower-level affiliates and allow them to gain notoriety and legitimacy.
The primary example was the finding that the Conti derivative group Zeon/Ryuk/Conti1. The group primarily functions as an autonomous “ghost group” that processes and offers top-tier network access to BlackCat (via 3AM ransomware), Akira, and LockBit 3.0 ransomware collectives. Zeon provides its own negotiation support center, phishing dissemination, and high-end initial accesses to external groups, which in turn supply their own locker, blog, negotiations, and data publishing, as well as any high-end accesses which it can not process due to the lack of pentesting skills.
Interestingly, Akira and LockBit (along with ALPHV) also handled outsourced operations for the threat group BlackSuit prior to and during its own transition from the Royal brand. REvil’s ex-pentesting team also was a ghost group for BlackSuit, but was integrated into BlackSuit’s structure during the rebrand.
At this point, LockBit is the leader in utilizing ghost groups. While having low-tier capabilities themselves and not being able to deliver major damage through their own team, LockBit was able to set long-term alliances with ex-Conti and BlackCat, enabling them to process and obtain high-end accesses and keep positive publicity regarding their capabilities.
Why is this a trend?
Threat groups are reliant on the existence and functionality of their shame blogs in order to successfully execute their ransomware operations, as otherwise they cannot threaten victims with intent to release stolen data to the public or facilitate negotiations. This makes these groups extremely vulnerable to Law Enforcement Actions (LEAs) which result in their blogs being shut down. By operating as a ghost group, Zeon becomes practically immune to one of the main threats of LEAs, as they operate through other groups’ blogs.
Established threat groups such as BlackSuit have also been outsourcing initial accesses to IABs (Initial Access Brokers), which allow the group to shift resources away from developing novel phishing campaigns.
2. Post-breach exploitation: “Double Jeopardy”
“Double Jeopardy” post-breach exploitation is the weaponization of a single attack multiple times by a threat actor or group. The name refers to a legal clause
that prevents a person from being charged multiple times for the same crime. With “double jeopardy” exploitation, this can include the following:
Claiming open-source data as a new attack: A threat actor uses publicly available data and claims it as novel.
- 2023 Example: Autonomous/Unaffiliated threat actors (sharing “leaks” on Telegram feeds which are actually taken from publicly available data)
Sharing victims: Multiple threat groups publish identical stolen data or claim the same attack while claiming they are the sole attacker.
- 2023 Example: Snatch & Nokoyawa (posting identical victim data on their respective shame blogs).
Reutilizing older data: The threat group either takes third-party data from a previous attack and claims it as a new direct attack on the third-party entity, or merely reposts data from a previous operation and claims it as novel.
- 2023 Example: LockBit 3.0 (posting third-party data leaks on their shame site and claiming as separate breaches, reposting data from previous thefts and claiming as new attacks)
Additional Note: Reutilization of older data as a trend has risen alongside the reutilization of threat TTPs in general. As noted throughout this review, 2023 threat groups and actors are increasingly utilizing existing tactics as well as data. One example of this is noted under the “Conti’s Legacy” section, where threat actors (such as Putin Team, ScareCrow, BlueSky, and Meow
) are likely modifying the open-source original Conti source code to deploy new attacks. The availability of open-source malware has increased in recent years as more threat groups’ source codes have been leaked online (Such as Conti,
LockBit 3.0,
and Babuk
).
Why is this a trend?
These tactics are most commonly used by threat actors in order to appear as though they have executed more attacks than they actually have, or that they were solely responsible for attacks which can be attributed to multiple groups.
3. Post-breach exploitation: Future Victimology
Another form of post-breach exploitation is “Future Victimology”—wherein data and accesses from previous attacks are utilized by threat actors to find and exploit future targets. For example, this may involve contacting business associates found within the contact lists of a hacked email, or exploiting information regarding a third-party company which is found within stolen data to later target that company.
The threat actors who most commonly employ this tactic are the BlackBasta group, who are known to use critical business information, internal business, and technology data, as well as hijacked cookies and credentials obtained from previous operations in order to obtain subsequent accesses for future attacks.
BlackSuit also utilized this tactic in 2023 following its rebrand to disrupt digital supply chains by targeting software code with the intent to later compromise retail and commerce clients.
Why is this a trend?
The use of “Future Victimology” exploitations significantly cuts down on resources and time needed to be spent by threat actors to seek out potential future victims. It is also more effective than broad “spray-and-pray” tactics (which involve blindly casting a wide net with attacks). An increase in notable credential stuffing attacks (which involve obtaining credentials from a data breach to log in to another unrelated service) may also coincide with the rise of this trend, as more threat actors begin to weaponize these post-breach exploitation tactics. 23andMe
and Paypal
both experienced significant breaches in 2023 wherein threat actors utilized this technique.
4. Actor Profile Diversification
This 2023 trend involved the integration of more non-Eastern European malware methodologies and groups into the ransomware sphere.
This includes the English-speaking group Scattered Spider’s rise to prominence, as well as ALPHV’s short-lived affiliation with the group (which may have led to the latter’s FBI takedown action). This trend also encompasses the rise in popularity for DarkGate loader (a non-Russian QBot replacement used by BlackBasta and multiple others whose developer is suspected to be from the Philippines) and BlackNET (a botnet tracked by RedSense to a developer in Kuwait).
Why is this a trend?
Non-Russian malware and non-Russian threat groups tend to operate using a different school of thought in regards to threat operations. This school of thought prioritizes universalism and versatility, as opposed to the intense but narrow specialization prioritized by their Russian counterparts. This differing psychology offers the potential of “fresh blood” into the threat ecosystem which is needed in order for the ecosystem to evolve.
5. Attempts to Weaponize AI
Threat actors have made numerous attempts to capitalize on the increasing popularity of AI technology (such as chatbots, image, voice, and text generators).
Although the development of this trend began in 2022, threat actors notably attempted numerous times to weaponize AI in throughout 2023:
- The year began with a post-Conti group developing an impersonation scheme, in which a fake conglomerate company was created which featured a malicious AI-powered chatbot used to convince victims to open malicious attachments.
- This group later utilized access to WormGPT, a malicious version of ChatGPT, which was used by the group to develop novel TTPs and social engineering campaigns.
- In September 2023: The English-speaking group Scattered Spider begins to utilize voice phishing/”Vishing” (the use of AI to disguise a threat actor’s voice and impersonate a co-worker). Scattered Spider has been known to utilize Voice Phishing tactics to impersonate IT personnel and gain initial network access.
- Deepfake phishing: Throughout the year, threat actors were even seen developing complex impersonation tactics such as deepfake phishing
to impersonate company employees.
Why is this a trend?
Although general AI use is relatively new to the general public, the technology has been exploited by malicious actors almost as quickly as it has been developed, as evident by the creation of WormGPT and the similar FraudGPT shortly following the release of ChatGPT. As AI becomes capable of executing more complex tasks, threat groups will continue to exploit the technology in order to automate more labor required for threat operation development. This will ultimately preserve threat group time and resources as well as potentially lower the entrance barrier to cybercriminal activity.
6. Black SEO Techniques
“Black SEO” techniques (short for “black hat SEO”) refer to a set of Search Engine Optimization techniques that violate set search engine regulations.
This encompasses tactics such as “Malvertising”
, or the use of online ads to spread malware, which has experienced a massive surge in the past year. This is primarily due to increased exploitation of Google Ads to spread (primarily stealer) malware such as AuroraStealer, IcedID, Meta Stealer, RedLine Stealer, and Vidar.
Similar to Malvertising, “SEO poisoning”
or “Search Engine Optimization poisoning” is currently experiencing a surge among threat actors. SEO poisoning involves influencing search engine results to push their malicious links higher in ranking—Because current Google Ads often appear above top search results and are difficult to distinguish from other legitimate links, users are more easily tricked into engaging with malvertising content.
In Spring 2023, ransomware operators also began to weaponize Google “dorking”
(the use of highly-tailored search queries that are run through Google’s search engine in order to find publicly indexed website data) in order to find and exploit system weaknesses.
The “pioneer” in these operations was Royal.
Why is this a trend?
As SEO optimization has exploded among advertisers, numerous techniques have been developed which are used by legitimate companies to boost themselves to the top of search results. A surge in the efficacy and prevalence in these legitimate techniques also enables SEO to be increasingly exploited by threat actors.
7. Intensifying Public Shaming
In 2023, “shaming” tactics utilized by threat actors to coerce victims to pay ransom intensified, and became more unique in order to attract media attention.
The primary example of this in 2023 was BlackCat/ALPHV, who experimented with novel shaming tactics such as publishing explicit patient photographs and PII on its public shame blog, writing extensive and aggressive shame blog entries detailing its negotiations with victim companies, publishing screenshots of these communications (including emails, documents, and video conferences related to the company’s response to the breach), filing an SEC report against a victim company for failure to notify the SEC of their attack, creating a public clone website of a victim featuring stolen data, and creating a searchable database of stolen data and advertising it to employees and clients of victim companies.
These tactics likely contributed to the use of an international takedown action against ALPHV in December 2023.
Why is this a trend?
In an attempt to overcome a low payout ratio for ransom extortions, threat actors have taken to the public sphere, becoming increasingly creative and aggressive in order to attract widespread attention to attacks in hopes that victim companies will be shamed by the public into meeting their demands.
8. “Takedowns”/LEAs
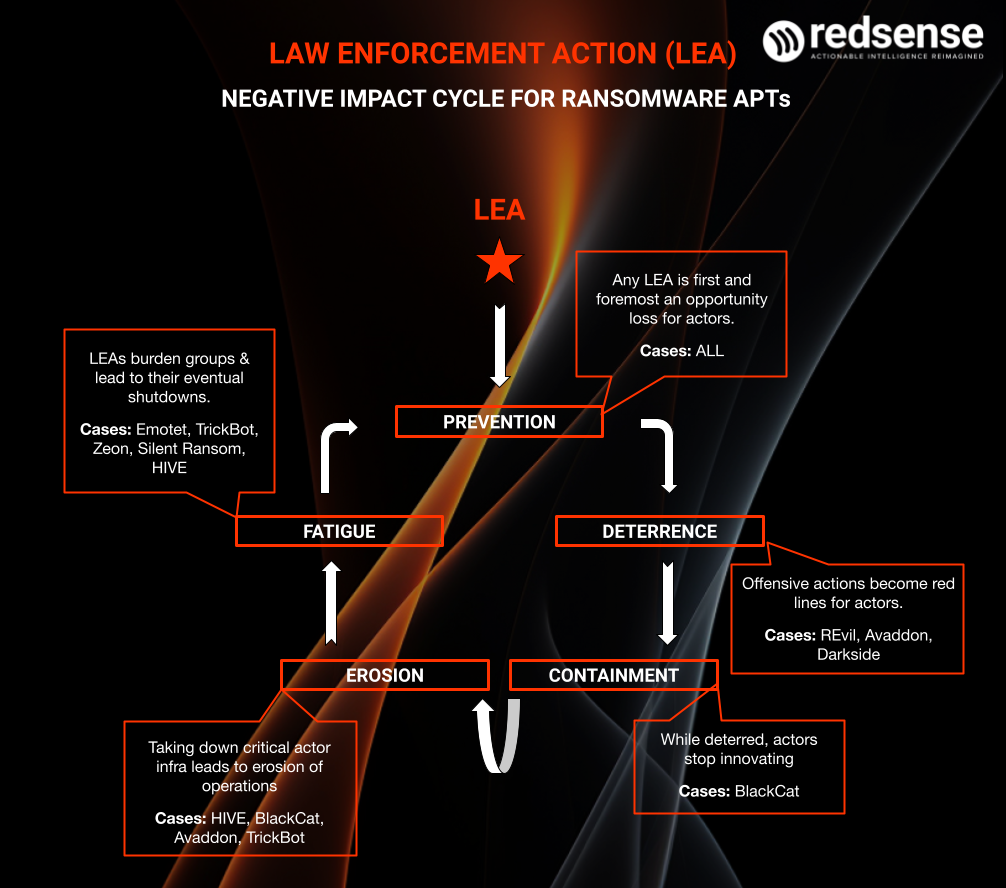
Infographic detailing the negative impact cycle for ransomware APTs [Source: RedSense]
A number of significant “takedowns”/Law Enforcement Actions (“LEAs”) occurred in 2023 with the intention of dismantling or corroding threat actors.
This included HIVE
(disrupted by the FBI in January 2023), QBot
(BlackBasta’s primary botnet, which was temporarily disrupted by international law enforcement in August 2023), Trigona
(disrupted by pro-Ukrainian hacktivists in October 2023), RagnarLocker
(disrupted by international law enforcement in October 2023), and ALPHV
(disrupted by international law enforcement in December 2023).
This is a massive jump in prevalence for LEAs: the last major takedowns occurred in 2021 with REvil and Avaddon, and in 2020 with TrickBot.
Why is this a trend?
Law enforcement agencies have heavily prioritized cracking down on ransomware groups in 2023. This is due to a wide variety of factors, such as improved digital investigative tools. One major factor is the aggregation of threat actor patterns over time, which subsequently leads to a domino effect: In other words, progress is made slowly for an extended period as threat actor activity is tracked and analyzed. However, LEAs against one threat actor or group can quickly give way to a streak of larger takedowns. In addition, law enforcement has become increasingly aware of threat actor dependence on shame blogs in order to continue streamlined operations, leading to an increased focus on taking the blogs down.
9. Conti’s Legacy
Although the threat syndicate Conti was officially dismantled in 2022, its actors still operate many of the most prolific threat groups of 2023, such as BlackSuit and BlackBasta. This is particularly true following the disruption of HIVE and ALPHV.
Notably, the groups 3AM, LockBit 3.0 and Akira were identified by RedSense to outsource their top-tier pentesting operations to Zeon (formerly known as Conti1) due to the latter’s elite skill level as a team. This discovery positioned Conti’s ex-pentesting team at the forefront of many top-tier attacks previously attributed to other threat groups.
Other groups that are not technically Conti derivatives also continue to work with active ex-Conti affiliates. For example, pentesters of the threat group REvil (which was dismantled in 2021) now operate under the BlackSuit name.

Infographic depicting shifts in attack methodologies throughout 2023 for top-tier threat groups. Note LockBit’s associations with Zeon and Royal/BlackSuit, as well as BlackCat’s ties to IcedID (which is integrally tied to Royal/BlackSuit).
Why is this a trend?
Many of Conti’s developers possess an elite skill level which is difficult to match or replace by novel threat actors, making their skillset extremely high-demand and therefore high-reward. Also, because the Conti source code is publicly available, threat actors are able to widely utilize and modify the original Conti source code in order to develop new ransomware strains (such as in the instance of Putin Team
).
10. Locker/Loader Experimentation
A number of threat groups experimented with new or existing malware lockers throughout 2023, in an attempt to maintain relevancy and avoid predictability and detection.
One primary example of this trend includes Royal’s experimentation with numerous lockers and loaders, from Ares and 3AM to BlackSuit and custom-written malware. RedSense’s findings have indicated that their locker experimentation was related to a competition to choose a new primary locker malware following the BlackSuit transition.

Infographic detailing multiple shifts which occurred following Royal’s transition to BlackSuit, including their change in payload which resulted from experimentation prior to the rebrand.
BlackBasta has notably utilized Pikabot and DarkGate as replacement malware since the temporary FBI takedown of QBot in late August 2023. According to RedSense’s internal visibility into the threat group BlackBasta, the group plans to relaunch QBot this month in January 2024. The group also utilized the stealers Redline and Vidar as part of a novel stealer-to-loader killchain experimentation.
11. Zero Days
Citrix Bleed (CVE 2023-4966)
A number of critical Zero-Day vulnerabilities were discovered and exploited widely in 2023. By far the most prolific and notorious was Citrix Bleed (CVE 2023-4966)
, which allows threat actors to hijack user sessions. This vulnerability is confirmed to have been exploited by BlackSuit, BlackBasta, ALPHV, LockBit 3.0, Zeon, and a number of independent threat actors throughout 2023. Notable victims of Citrix Bleed exploitation have included government and defense entities such as Boeing and ICBC Financial Services.
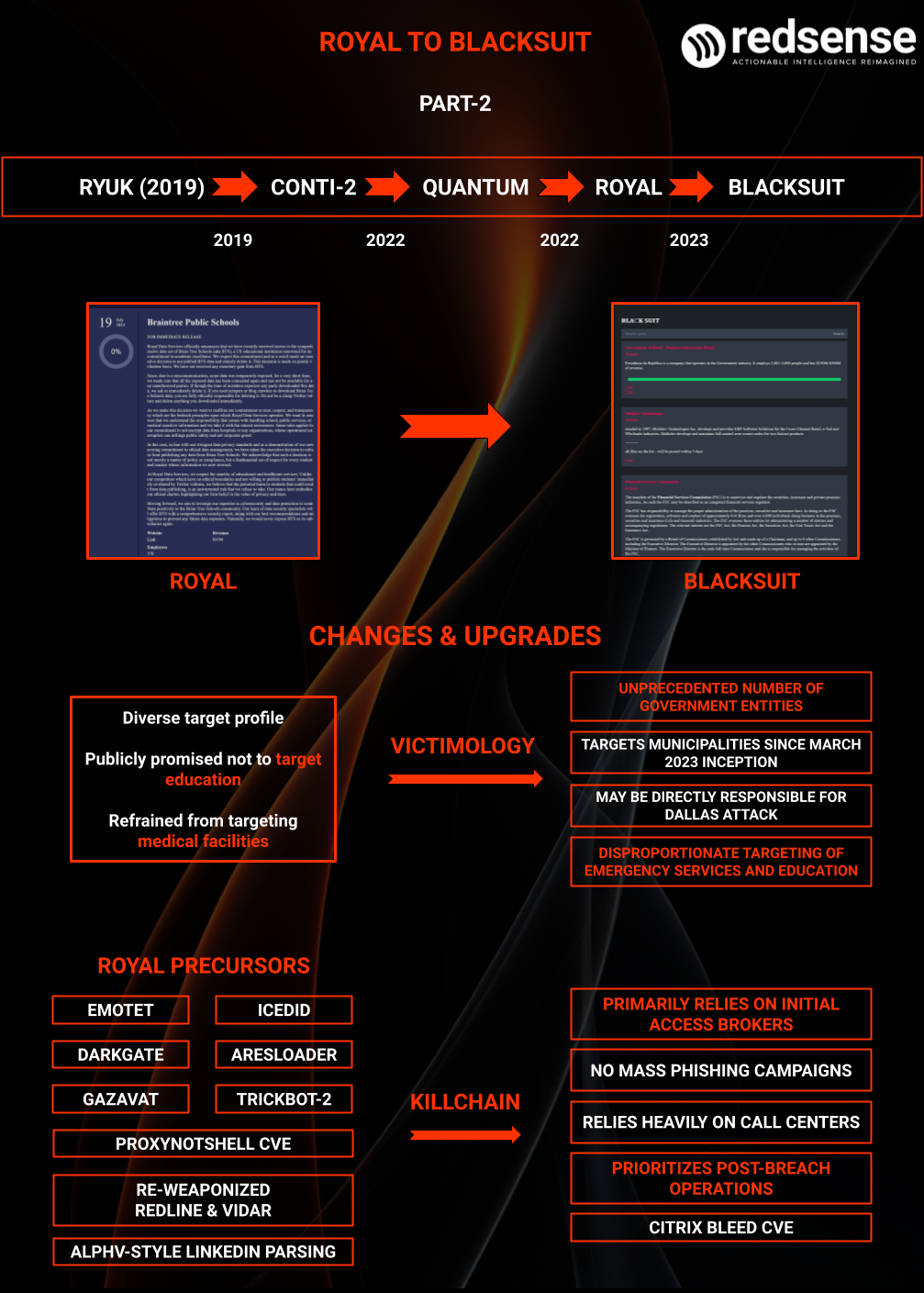
Infographic depicting multiple changes made during Royal’s transition to BlackSuit. Note that Citrix Bleed is specifically mentioned as a BlackSuit precursor due to high levels of targeting from the group. [Source: RedSense]
Why is this a trend?
Threat groups are known to target vulnerabilities in widely-used software to maximize their reach and impact. Due to the widespread use of the affected software NetScaler ADC and NetScaler Gateway, as well as the fact that the patch was only released in October 2023 (meaning any devices not updated prior to then were vulnerable), many thousands of corporate devices were left exposed, giving threat actors a massive attack surface to exploit the vulnerability.
Additional Note: Other examples of critical CVEs which were highly exploited in 2023/early 2024 include:
- CVE-2023-6549 (DDoS)
and CVE-2023-6548 (RCE):
Similar to Citrix Bleed, These vulnerabilities affect the Netscaler management interface and may result in either denial-of-service or remote code execution attacks. CVE-2023-6549 could also be leveraged to obtain initial access using brute force or fuzzing attacks.
- CVE-2023-41990 (iMessage 0-Click)
: Although this RCE vulnerability has existed since 2019, it is the beginning of a complex attack chain affecting iMessage which utilizes four different zero-days in total (CVE-2023-41990
, CVE-2023-32434
, CVE-2023-38606
, and CVE-2023-32435
to gain root privileges of victim Apple devices.
- CVE-2023-40088 (Android 0-Click)
: Android also found a critical vulnerability in its System component which could lead to unauthorized RCE without user interaction.
- CVE-2023-51467 (OFBiz)
: RCE vulnerability affecting the web framework Apache OFBiz.
- CVE-2023-45849 (Helix Core Server)
: Four critical vulnerabilities recently discovered for a common code management software, one of which is an unauthenticated RCE vulnerability
- CVE-2023-29324 (Microsoft)
: Security Bypass vulnerability, utilized by the threat group Fancy Bear to gain access to Microsoft Exchange accounts.
Bonus Section: Interconnectivity
Numerous connections between known threat actors and groups were established by RedSense in 2023. This includes the following:
Ransomware <-> Ransomware Connectivity
Zeon
- Zeon <-> 3AM: Based on Inrinsec and RedSense findings, Zeon (Team1) has established communication with 3AM ransomware, which they use as an intermediary in their work with other groups.
- Zeon <-> Larger low-tier collectives: Zeon primarily functions as an autonomous “outsourcing group” that handles large-scale threat operations for Akira, LockBit, INC, and BlackCat (until its takedown).
Royal/BlackSuit
- LockBit 3.0 <-> Royal/BlackSuit
- The majority of Royal’s high-ranking operators, including its chief pentester and its negotiator, were found to be using LockBit’s affiliate accounts and proprietary locker. This is a result of a systemic partnership between Royal’s and LockBit’s admins.
- ALPHV <-> Royal/BlackSuit
- ALPHV/BlackCat worked in conjunction with Blacksuit in 2023, helping to drop the group’s locker while the group was still in the process of rebranding from the Royal name.
- ALPHV <-> Scattered Spider
- ALPHV partnered with Scattered Spider for a short period in 2023. However, a member of Scattered Spider may have subsequently led to ALPHV’s international LEA takedown.
- REvil <-> Royal/BlackSuit
- After its takedown in Russia in 2022, REvil’s team operated as an autonomous group contracted by Royal for pentesting operations. In 2023, they were consumed by Royal.
- BlackSuit <-> Unaffiliated Threat Actors (Aliases redacted)
- One of BlackSuit’s primary access methods post-rebrand is the use of IABs, or Initial Access Brokers. This allows the group to achieve initial access to victim systems without having to develop a threat campaign.
- Snatch <-> Nokoyawa
- Snatch and Nokoyawa were found to be sharing shame blog victims, with several indicators pointing to Nokoyawa being a “false flag” group pretending to be a Chinese APT.
- Nokoyawa <-> Royal/BlackSuit
- Nokoyawa targeted Italian organizations with malicious Microsoft Excel files that deployed the malware IcedID. This attack was noted by RedSense in 2023 to include identical code to one of the projects found in a collective malware development GitLab used by Royal’s key developer, making it likely that Royal used Nokoyawa as a publishing group for these attacks.
Ransomware <-> Malware Connectivity
- Nokoyawa
- IcedID: Nokoyawa targeted Italian organizations with malicious Microsoft Excel files that deployed the malware IcedID.
- Rapid/Amadey: Nokoyawa has also utilized both Rapid Ransomware
and Amadey
ransomware, which are monitored by RedSense.
- Royal/BlackSuit
- Akira (affiliate locker malware): Akira began active locker development in March 2023, when Royal began actively engaging various threat groups to create a new locker for their rebrand. However, they decided against further use of the Akira locker by June 2023.
- BlackSuit (proprietary locker malware): The new BlackSuit malware payload was developed beginning in Spring 2023 and was finished in Fall 2023. RedSense tracked the development of the malware using group visibility.
- IcedID/Redline/Ares/CryptInject/Seheq: In 2023, RedSense found a number of malware strains uploaded by AresLoader during analysis of the loader’s integration into Royal and post-Conti operations. These strains included Redline Stealer, Seheq, CryptInject, Leonem, and IcedID.
- BlackBasta
- QBot: Until late August 2023, QBot was BlackBasta’s primary botnet. The botnet has been taken down by law enforcement, but the group is currently planning a relaunch sometime in early 2024.
- Redline, Vidar: One of the replacements utilized by BlackBasta after QBot’s takedown was a stealer-loader infection chain which included stealer malware such as Redline and Vidar.
- DarkGate: The current primary replacement tool for QBot. DarkGate was selected by BlackBasta due to its ability to bypass protection systems and multiple restoration and protection capabilities, making it a sufficient substitute for QBot’s capabilities.
- Cl0p
- human2.aspx (WebShell): RedSense’s analysts were able to successfully replicate the main elements of the CVE-2023-34362 (MOVEit Zero-Day) post-exploitation killchain in June 2023. This included writing the webshell (a malicious script that enables threat actors to compromise a victim’s web server) human2.aspx to the victim’s file system.
- Botnets & Ransomware IABs
- BlackNET, KratosKnife, HookBot, LokiBot, Amadey, Mystic, Medusa (stealier), and Rhadamanthys: In 2023, RedSense obtained numerous findings related to a number of botnets which are purchased and utilized by independent threat actors who are unaffiliated with a larger threat collective. These actors may serve as Initial Access Brokers (IABs) for groups such as BlackSuit. These findings included discovery of the panel builder and source code for BlackNET, the botnet panel for HookBot, the source code and logs for KratosKnife, multiple Amadey servers, and the panel and source code for LokiBot. These accesses have been analyzed by RedSense’s intelligence team to better understand how threat actors utilize their capabilities and parameters.