Smishing, a portmanteau of “SMS” and “phishing,” is a type of cyber attack where scammers use text messages to trick recipients into divulging personal information, financial details, or security credentials. Unlike traditional phishing which primarily uses emails, smishing exploits our reliance on smartphones, the generally weakness of SMS security filters, and the perception that text messages are more trustworthy than emails.
Common Tactics
Fake Alerts - These messages, often appearing to be from banks or credit card companies, claim there is a problem with your account and prompt you to click a link or call a number.
IT and Service Desk Impersonations – Requests that appear to be from a trusted department or coworker asking you for information or ask. Examples of this include recent “Okta”, “SSO”, “ServiceNow” themed campaigns such as Scattered Spider.
Executive Impersonations – Fraudulent time-sensitive requests from your boss or another executive who are often “out of the office and need help”.
Delivery Scams - Texts pretending to be from postal services, asking you to click a link to track a package or update delivery preferences.
Tax Scams - Messages claiming to be from tax authorities, prompting action regarding refunds or unpaid taxes.
Prize Scams or Gift Offers - Notifications of winning a contest or receiving a gift, with a link to claim it or requesting personal information.
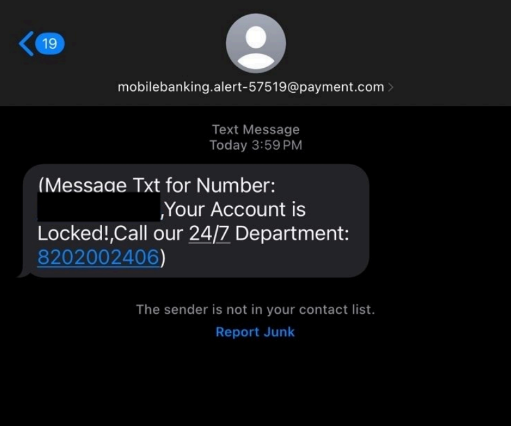
Example of Smishing
How to Identify Smishing
Check the Sender – Always verify the sender’s contact details.
Watch for Urgent or Threatening Language - Messages that create a sense of urgency or threaten dire consequences.
Requests for Personal Information - Legitimate organizations typically don’t ask for sensitive information via text.
Verify Links - Be wary of messages from unknown numbers or containing links with unfamiliar or misspelled URLs.
Protective Measures
Report Suspicious Messages – If you receive a suspicious text, report it to your IT department or the appropriate authority.
Routinely Educate Employees – Train staff to recognize and report new smishing tactics and threats
Enable Advanced Authentication – All corporate applications should avoid simple passwords and use methods such as two-factor or multi-factor authentication. (However, remember that SMS authentication is prone to the very real threat of SIM-swapping)
Never Click on Suspicious Links – Don’t let your curiosity overcome your gut feeling of mis-trust.
Don’t Reply to Suspicious Messages – Just responding can confirm to the scammer that your number is active.
Verify the Source – If in doubt, contact the organization directly using a trusted method, not the details provided in the message.
Install Security Software – Use mobile security software and keep your phone’s operating system up to date.
Conclusion
Always stay vigilant. If a text message seems suspicious, it’s better to err on the side of caution and verify its authenticity through secure, independent means. Remember, protecting your personal information is key in the digital age.
See also: Understanding Vishing