Content Category: Publications
Reports and advisories from the RedSense CTI team.

Lockbit Persists
Despite the international takedown of LockBit nearly a year ago, its influence continues to shape the ransomware ecosystem. While the group itself has collapsed, its techniques, tools, and even its former members have been absorbed into other threat groups, ensuring that its legacy endures.
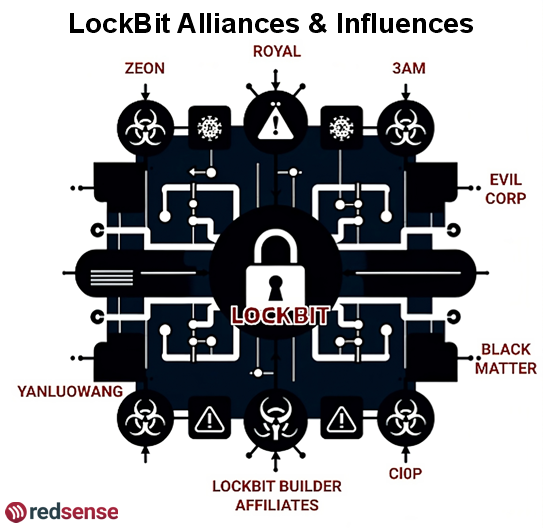
LockBit - Persistent TTPs in the Larger Ecosystem
Despite the international takedown of LockBit nearly a year ago, its influence continues to shape the ransomware ecosystem. While the group itself has collapsed, its techniques, tools, and even its former members have been absorbed into other threat groups, ensuring that its legacy endures. From the proliferation of its leaked ransomware builder to the deceptive tactics it pioneered—like inflating victim numbers and weaponizing false breach claims—LockBit’s impact remains deeply embedded in modern cyber threats. In this blog, we analyze how LockBit’s tactics persist and evolve, providing a crucial look at the ongoing risks and adaptations within the ransomware landscape.
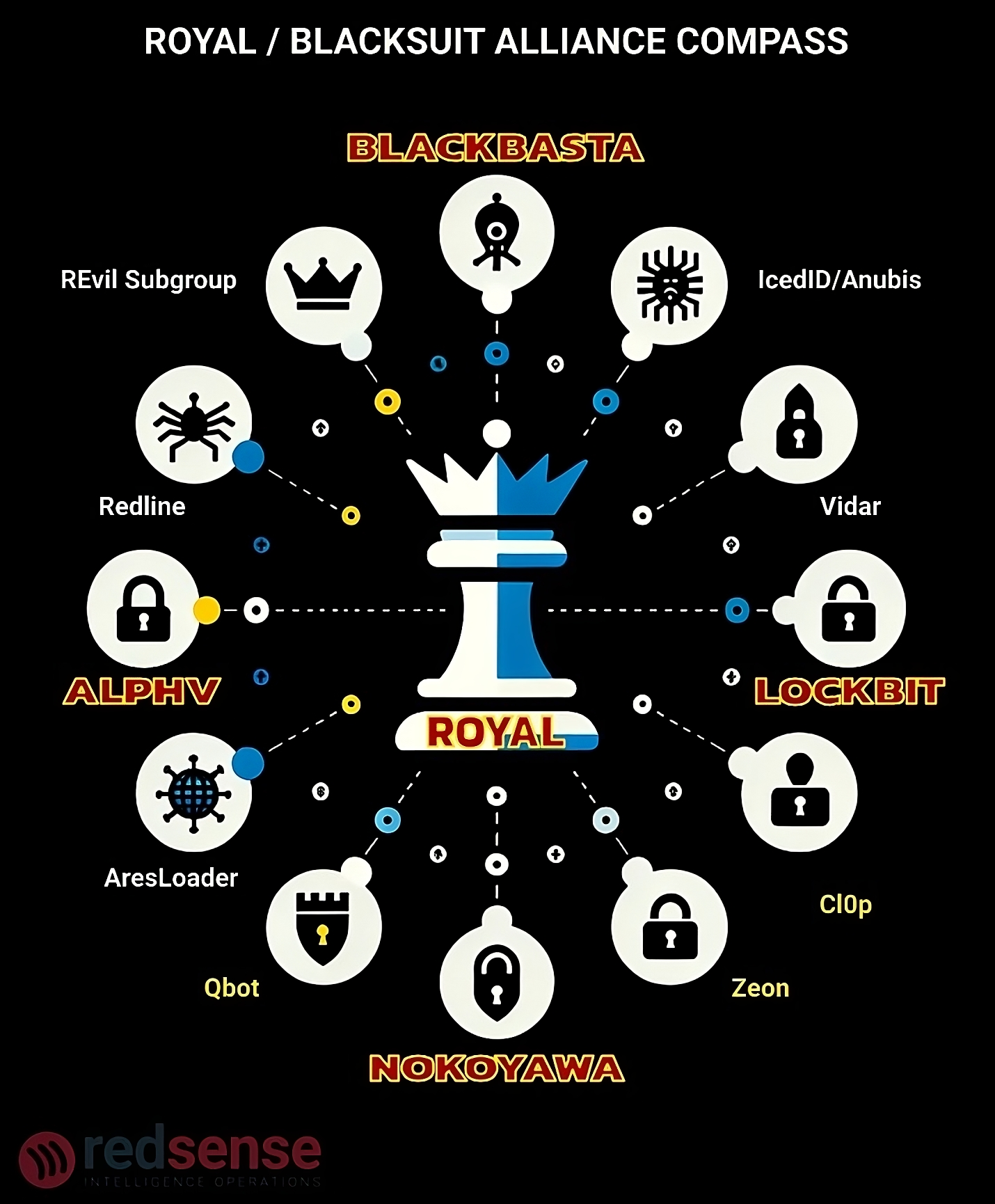
From Royal to BlackSuit
Based on previous RedSense reporting, we explore the evolution of the Russian-speaking ransomware group known as BlackSuit, formerly operating under various aliases, including Royal and Conti-2. We delve into the group’s history, highlighting key shifts in their tactics and organizational structure, particularly during their transition from Royal to BlackSuit.

The Threat of Corporate Cybercrime During the Holiday Season
As the year draws to a close, businesses worldwide gear up for the bustling holiday season. However, while companies focus on closing out their fiscal years, managing holiday promotions, or preparing for reduced staff levels, cybercriminals are gearing up for their own end-of-year surge. The holiday season, including New Year’s celebrations, presents a unique and lucrative opportunity for malicious actors to exploit vulnerabilities in corporate cybersecurity defenses.
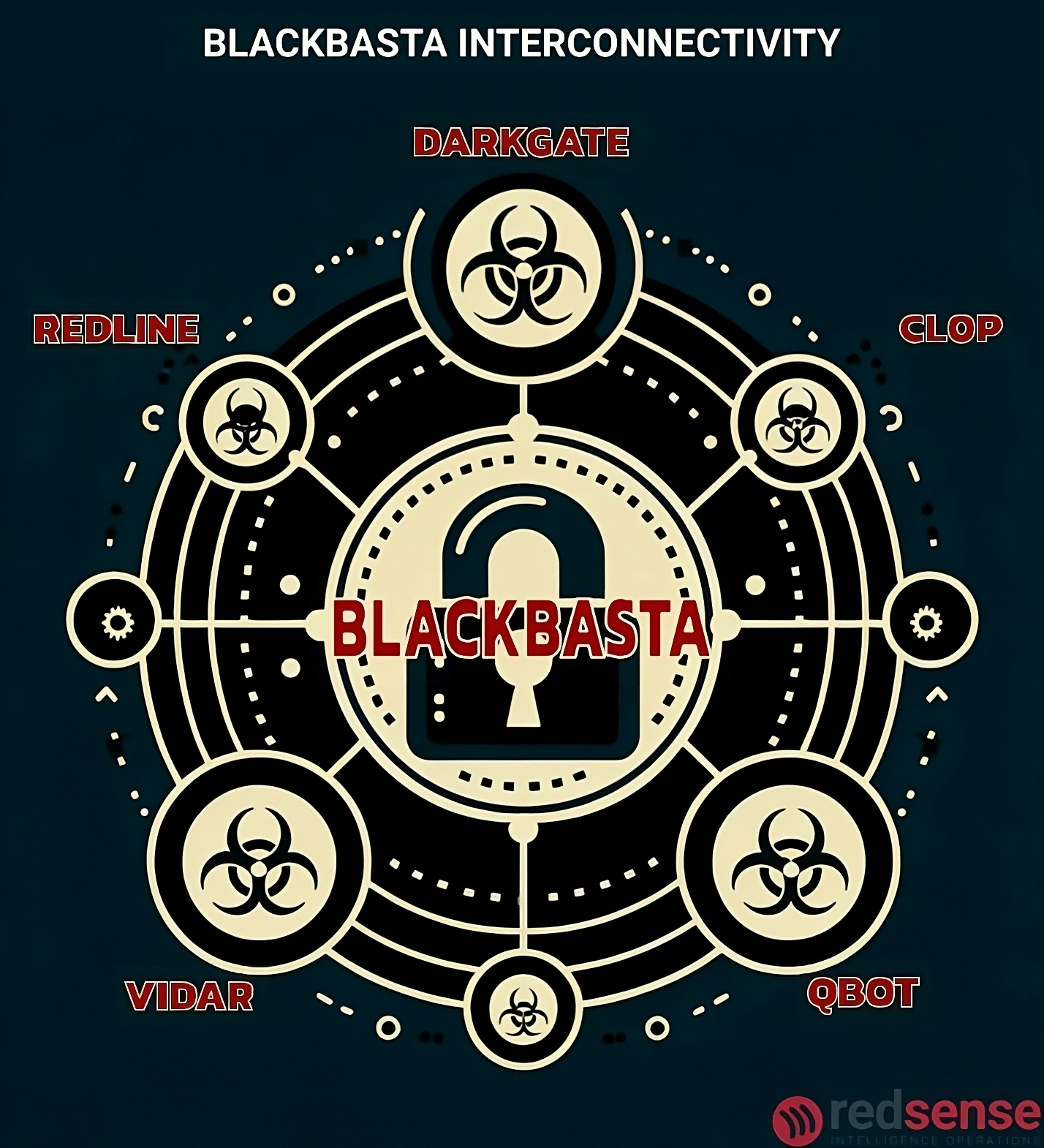
The Evolution of BlackBasta Malware Dissemination
BlackBasta has evolved from relying on botnets like Qbot in 2022 to a hybrid model incorporating advanced social engineering by 2024. Initially influenced by Conti’s methodologies, the group adopted callback phishing and large-scale botnet use. Following the 2023 Qbot takedown, BlackBasta diversified, collaborating with DarkGate and exploiting platforms like Microsoft Teams. By 2024, it integrated targeted phishing and impersonation schemes, blending technical and social tactics. Drawing on post-Conti malware lab influences, BlackBasta has adapted to law enforcement pressures, establishing itself as a leader in ransomware innovation and resilience.

Threat Intelligence Use Cases for Legal
RedSense, in conjunction with law firm Norton Rose Fullbright, recently held a webinar exploring the potential of Cyber Threat Intelligence (CTI)in common legal and regulatory scenarios. The presentation looked at mitigating cyber risks and reducing legal exposure, ensuring compliance, and more rapidly responding to incidents involving sensitive and possibly exfiltrated data.

Common Cybercrime Attack Vectors
Cybercrime is a sophisticated global threat, if not pandemic, with corporations and government entities frequently in the crosshairs of malicious actors. The consequences of these attacks can range from financial losses and operational disruptions to reputational damage and national security risks. To effectively combat these threats, it is essential to understand the most common attack vectors used by cybercriminals.

The Importance of Defense in Depth: Lessons from the Recent CrowdStrike Outage
In the world of cybersecurity, even the most trusted tools can sometimes fail. This was underscored recently when CrowdStrike, an extremely well regarded cybersecurity company, inadvertently pushed a software update that impacted their customer’s systems and security services. While such incidents are rare, they serve as a reminder that no single piece of hardware or software is infallible. The reality is that failures, whether it be system outages or missed threat identifications, though infrequent, are an inevitable aspect of cyber defense technology.

Understanding CISA’s Traffic Light Protocol: A Guide to Responsible Information Sharing
In an era dominated by digital information and cybersecurity threats, the importance of responsible information sharing cannot be overstated. The Cybersecurity and Infrastructure Security Agency (CISA) has endorsed a system known as the Traffic Light Protocol (TLP) to facilitate secure communication channels among industry stakeholders. This protocol provides a structured framework to enhance cooperation while ensuring that sensitive information remains protected.

Update on Recent Healthcare Cyberattack
In February of this year, following a cybersecurity incident at Change Healthcare, RedSense reviewed its telemetry data for indicators of adversary activity and tactics. We detected traffic that suggested a technology vendor and a recently reported vulnerability might be involved. We are pleased to announce that, after a thorough investigation by the vendor, United Health Group, forensic experts, and law enforcement, the vendor ultimately determined that its product was not the source of vulnerability in the Change Healthcare incident. We commend the vendor for their dedication to security and efforts to clear their solution from suspicion. This demonstrates the humility and transparency that all technology vendors should aspire to. We appreciate their updates, which allowed us to remove public comments suggesting their technology was potentially misused in the attack.

Q1 2024 RedSense Threat Briefing
The Winter 2023-2024 RedSense Threat Briefing provides updates on threats and intelligence for the final months of 2023 and the early part of 2024. It covers key areas including visibility updates, the current overall instability across the threat landscape, the decline of ransomware, emerging attack methodologies, analyses of victim patterns, and updates on important CVEs. It also offers forecasts on threat trends for the remainder of 2024.

LockBit Story: A Three-Year Investigative Journey
LockBit, until its recent downfall, was a standout in the ransomware-as-a-service (RaaS) landscape, notably enduring the RaaS model crisis that saw the collapse of many other groups between 2021 and 2022. While these competitors faltered, LockBit survived and thrived into early 2024, showcasing remarkable resilience. RedSense’s extensive investigation into LockBit’s durability, grounded in SIGINT, telemetry analysis, forensics, incident reviews, and malware reversal, demystify its resilience without succumbing to speculation.

Yearly Intel Trend Review
RedSense is excited to present our first “Yearly Intel Trend Review” for 2023! This is a summary review taken from our year-long project: The Ransomware APT White Paper—a 200-page cumulative research covering our five-year insights into ten top-tier ransomware groups serving as the backbone of today’s ransomware economy. The complete White Paper will be available for all RedSense customers in January 2024.
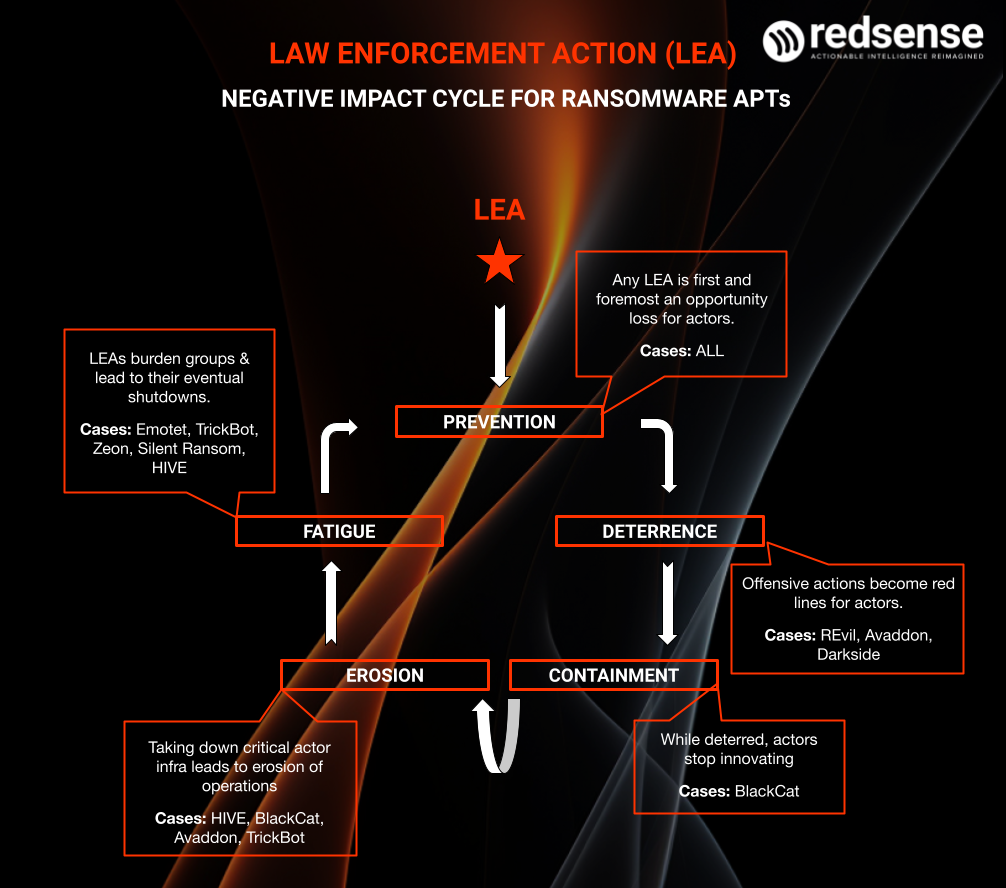
How Law Enforcement Actions Break Down Ransomware (featuring a Black Cat)
Early in the morning on Thursday, December 7th, my team at RedSense and I learned that a federal offensive was taking place against AlphV (aka BlackCat)’s infrastructure and had subsequently downed its servers. I share my personal thoughts on what long-term impacts a Law Enforcement Action (LEA) can have on the threat ecosystem at large.

November 2023 RedSense Threat Briefing
RedSense has released its November 2023 Threat Briefing. The summary published here constitutes a brief glimpse of the comprehensive insights available to our subscribers. The full report contains more extensive and detailed threat intelligence provided exclusively to our RedSense Advantage and RedSense As-a-Service clients on a regular basis.

Don’t Trust Your Ears
Vishing, a blend of “voice” and “phishing,” is a type of social engineering attack where scammers use phone calls to trick individuals into disclosing sensitive information. This technique can be particularly effective when the scammer impersonates a trusted authority, such as an IT support or service desk professional.

Your Phone May Be Lying to You
Smishing, a portmanteau of “SMS” and “phishing,” is a type of cyber attack where scammers use text messages to trick recipients into divulging personal information, financial details, or security credentials. Unlike traditional phishing which primarily uses emails, smishing exploits our reliance on smartphones, the generally weakness of SMS security filters, and the perception that text messages are more trustworthy than emails.

Artificial Intelligence in Cybersecurity
The greatest irony of current technology is that threat actors around the world are using artificial intelligence to more convincingly impersonate humans. That’s right, ChatGPT – a machine! – is enabling malicious activity like email phishing attacks. One might wonder what commentary Alan Turing would offer on this development.

October 2023 Redsense Threat Briefing
We are publishing a summary of our RedSense Threat Briefing for October 2023. This summary is just a small sample of the information RedSense customers receive on a regular cadence in much greater detail as part of either RedSense Advantage or RedSense As-a-Service for Cyber Threat Intelligence.

Holidays Routine
Naughty or nice, there’s a few things in cyber circuits that won’t change in this year’s Holiday Season. Threat actors are financially motivated, driven by human needs, and the holidays are expensive.

Advanced Adversary SSO Abuse
Low and slow Multi-Factor Authentication (MFA) exploitation abounds, as adversarial campaigns target exposed Single Sign-On (SSO) endpoints (e.g., Centralized Authentication Services) throughout August and September

Healthcare Still Under Threat
Since early 2022, leading security industry experts have made broad estimations that ‘ransomware is on the decline’, but did they properly contextualize their data and findings? Given destabilization from the Russia-Ukraine conflict and tightening U.S. and EU law enforcement activities, ‘ransomware is on the decline’ proponents underestimate their adversaries’ motivations, resiliency, and abilities to support persistent criminal operations.

Ransomware is Dead, Long Live Ransomware!
It seems to be a common misconception in business today that ransomware is dead or dying. The perception is that we haven’t seen a huge daily deluge of new major businesses making eight figure payments to prolific centralized operations in the way that they were over the last few years. Incidents like Medibank feel less common. This perception is inaccurate at best, and dangerous at worst.

VOIP Ecosystems: A Deep Dive
The methods enclosed in this write up can be used for several different types of malicious activities from call center support scams to just generic vishing campaigns.

Silent No More
Red Sense routinely collaborates with Industry and open source researchers. We are honored to republish an article by Dissent Doe (@PogoWasRight).

Daixin Hits Healthcare
Over the last several months, Red Sense has observed the growing threat of Daixin Team, who have successfully targeted multiple U.S. Healthcare victims.

Insights Into BlackBasta
Blackbasta is an active former-Conti staffed ransomware group that began organizing in late 2021 behind the dissolution of Conti’s centralized operations. Active operations were first observed in spring and summer of 2022, and there are several TTP similarities that carry forward from Conti to blackbasta operations.

Insights Into Lionkebab
During the final week of June 2022, Red Sense adversary space operations acquired a large victim list relating to criminal activities centered around a recent Confluence 0-Day, CVE-2021-26084.
