Content Category: Threat Actors
A “threat actor” is an individual or group responsible for initiating cyber attacks or security breaches with malicious intent.

Lockbit Persists
Despite the international takedown of LockBit nearly a year ago, its influence continues to shape the ransomware ecosystem. While the group itself has collapsed, its techniques, tools, and even its former members have been absorbed into other threat groups, ensuring that its legacy endures.
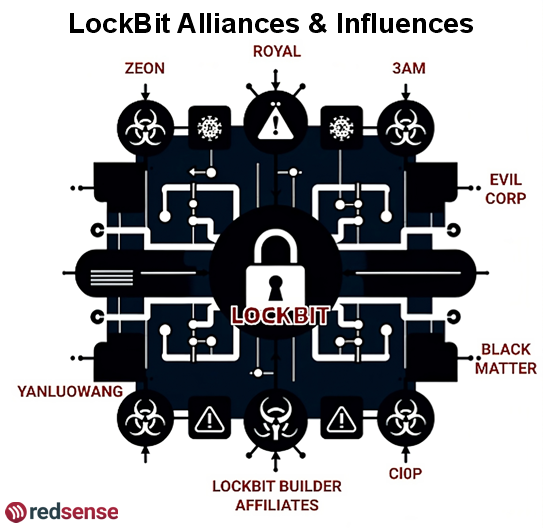
LockBit - Persistent TTPs in the Larger Ecosystem
Despite the international takedown of LockBit nearly a year ago, its influence continues to shape the ransomware ecosystem. While the group itself has collapsed, its techniques, tools, and even its former members have been absorbed into other threat groups, ensuring that its legacy endures. From the proliferation of its leaked ransomware builder to the deceptive tactics it pioneered—like inflating victim numbers and weaponizing false breach claims—LockBit’s impact remains deeply embedded in modern cyber threats. In this blog, we analyze how LockBit’s tactics persist and evolve, providing a crucial look at the ongoing risks and adaptations within the ransomware landscape.
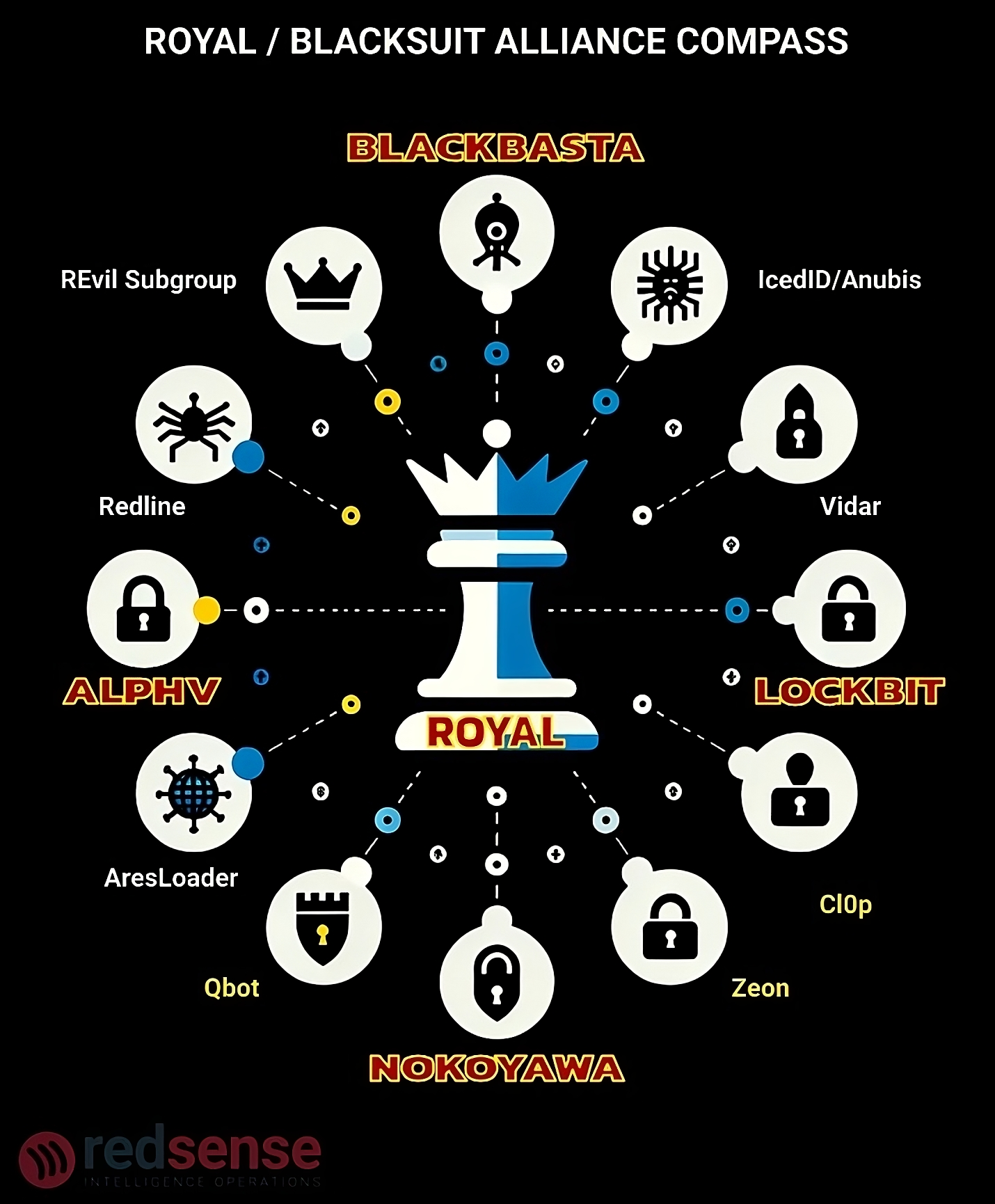
From Royal to BlackSuit
Based on previous RedSense reporting, we explore the evolution of the Russian-speaking ransomware group known as BlackSuit, formerly operating under various aliases, including Royal and Conti-2. We delve into the group’s history, highlighting key shifts in their tactics and organizational structure, particularly during their transition from Royal to BlackSuit.
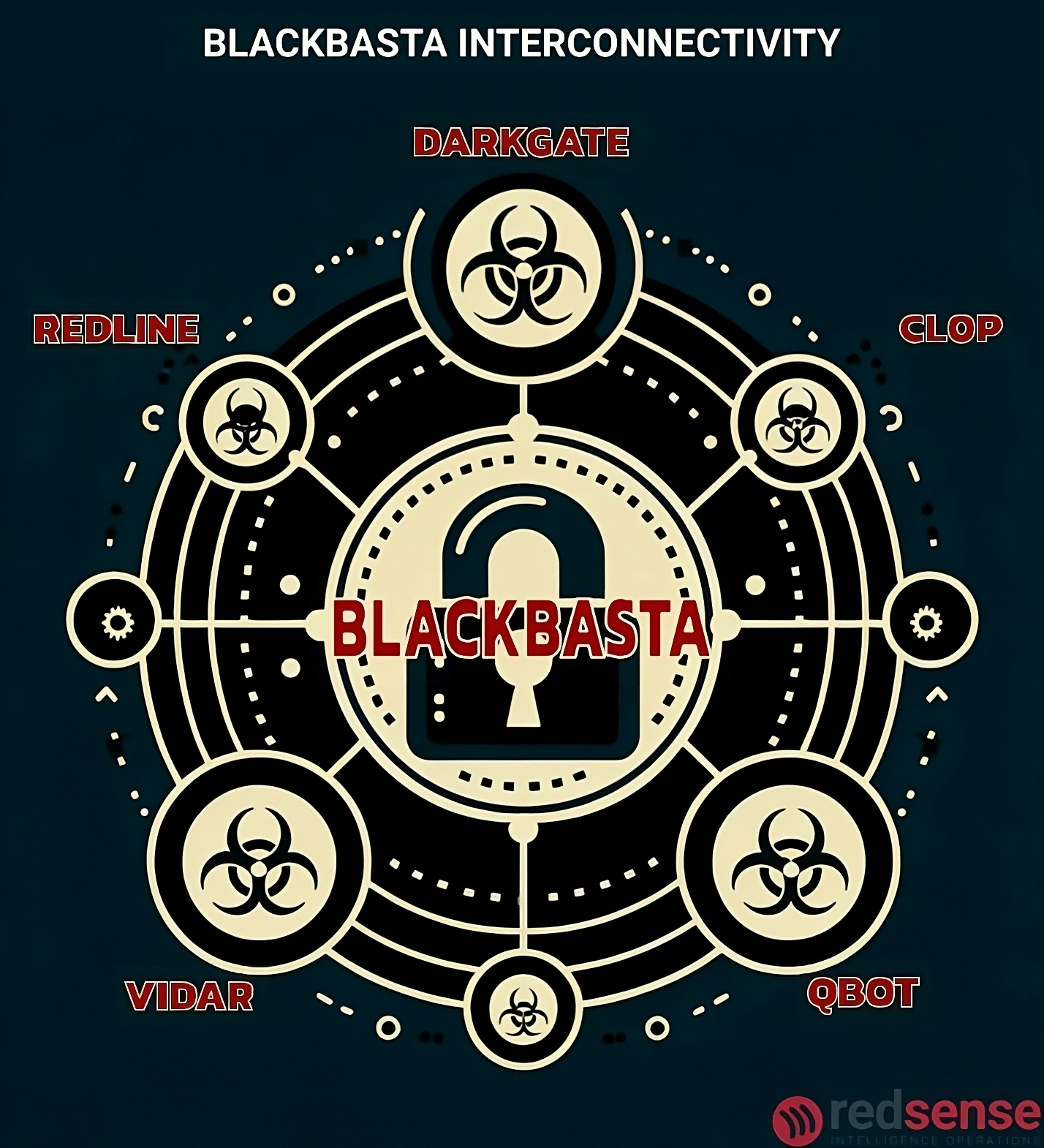
The Evolution of BlackBasta Malware Dissemination
BlackBasta has evolved from relying on botnets like Qbot in 2022 to a hybrid model incorporating advanced social engineering by 2024. Initially influenced by Conti’s methodologies, the group adopted callback phishing and large-scale botnet use. Following the 2023 Qbot takedown, BlackBasta diversified, collaborating with DarkGate and exploiting platforms like Microsoft Teams. By 2024, it integrated targeted phishing and impersonation schemes, blending technical and social tactics. Drawing on post-Conti malware lab influences, BlackBasta has adapted to law enforcement pressures, establishing itself as a leader in ransomware innovation and resilience.

Q1 2024 RedSense Threat Briefing
The Winter 2023-2024 RedSense Threat Briefing provides updates on threats and intelligence for the final months of 2023 and the early part of 2024. It covers key areas including visibility updates, the current overall instability across the threat landscape, the decline of ransomware, emerging attack methodologies, analyses of victim patterns, and updates on important CVEs. It also offers forecasts on threat trends for the remainder of 2024.

LockBit Story: A Three-Year Investigative Journey
LockBit, until its recent downfall, was a standout in the ransomware-as-a-service (RaaS) landscape, notably enduring the RaaS model crisis that saw the collapse of many other groups between 2021 and 2022. While these competitors faltered, LockBit survived and thrived into early 2024, showcasing remarkable resilience. RedSense’s extensive investigation into LockBit’s durability, grounded in SIGINT, telemetry analysis, forensics, incident reviews, and malware reversal, demystify its resilience without succumbing to speculation.

Yearly Intel Trend Review
RedSense is excited to present our first “Yearly Intel Trend Review” for 2023! This is a summary review taken from our year-long project: The Ransomware APT White Paper—a 200-page cumulative research covering our five-year insights into ten top-tier ransomware groups serving as the backbone of today’s ransomware economy. The complete White Paper will be available for all RedSense customers in January 2024.
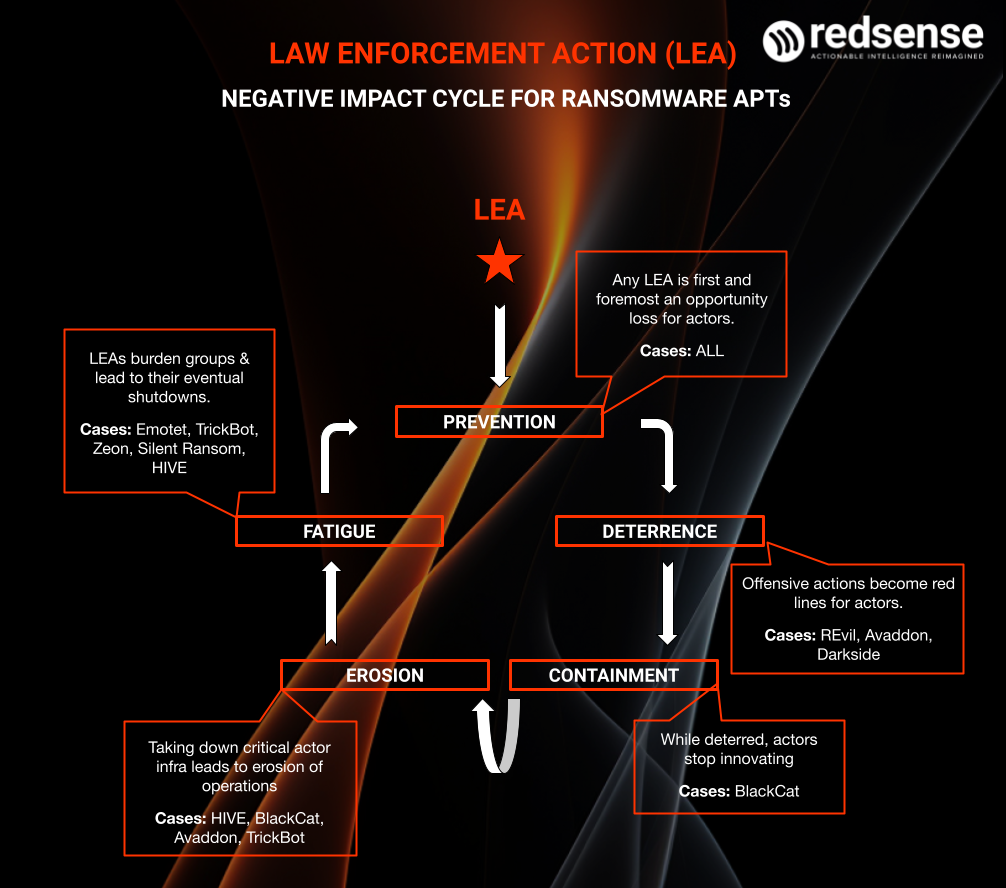
How Law Enforcement Actions Break Down Ransomware (featuring a Black Cat)
Early in the morning on Thursday, December 7th, my team at RedSense and I learned that a federal offensive was taking place against AlphV (aka BlackCat)’s infrastructure and had subsequently downed its servers. I share my personal thoughts on what long-term impacts a Law Enforcement Action (LEA) can have on the threat ecosystem at large.

November 2023 RedSense Threat Briefing
RedSense has released its November 2023 Threat Briefing. The summary published here constitutes a brief glimpse of the comprehensive insights available to our subscribers. The full report contains more extensive and detailed threat intelligence provided exclusively to our RedSense Advantage and RedSense As-a-Service clients on a regular basis.

October 2023 Redsense Threat Briefing
We are publishing a summary of our RedSense Threat Briefing for October 2023. This summary is just a small sample of the information RedSense customers receive on a regular cadence in much greater detail as part of either RedSense Advantage or RedSense As-a-Service for Cyber Threat Intelligence.

Weaponizing Artificial Intelligence Large Language Models (LLMs)
RedSense looks at how adversaries are working to leverage artificial intelligence large language models (LLMs) for malicious exploits.

Daixin Hits Healthcare
Over the last several months, Red Sense has observed the growing threat of Daixin Team, who have successfully targeted multiple U.S. Healthcare victims.

Insights Into BlackBasta
Blackbasta is an active former-Conti staffed ransomware group that began organizing in late 2021 behind the dissolution of Conti’s centralized operations. Active operations were first observed in spring and summer of 2022, and there are several TTP similarities that carry forward from Conti to blackbasta operations.
